Omdia, a global analyst and advisory leader, recently released a report called “How Extended Access Management (XAM) closes the gaps in security.” This report describes how existing approaches to access management have failed to address the security, budgetary, and compliance risks posed by unmanaged identities, applications, and devices.
“Legacy identity access management (IAM) and mobile device management (MDM) tools have fallen short of providing security while enabling a productivity-driven and innovative workforce. These tools were designed for a world where IT controlled every application, device, and tool in use, and employees had no digital free will or choice in how they did their work. In today’s world, employees freely adopt the tools and devices they need to be the most productive, regardless of whether they are provisioned or managed by their organization. As a result, untrusted and unmanaged forms of access proliferate across these devices and apps.” - Omdia, “How Extended Access Management (XAM) closes the gaps in security”
Omdia’s report goes on to recommend five strategies for organizations to address these shortcomings and succeed in a world that has been transformed by SaaS, BYOD, and AI.
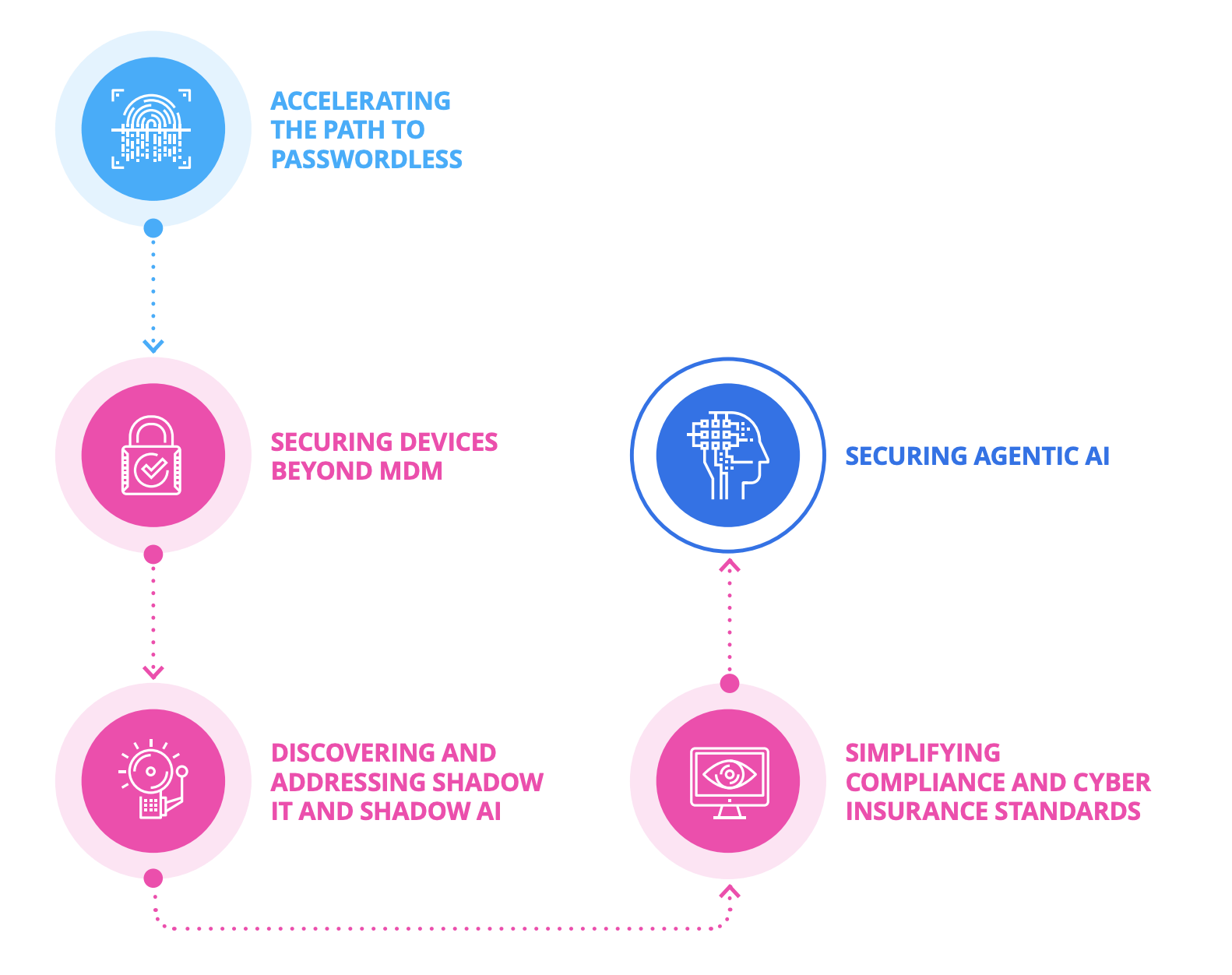
In our previous blogs in this series, we’ve covered Omdia’s first three strategies:
In this post, we’ll explore the fourth strategy: Simplifying compliance and cyber insurance standards.
Why compliance and cyber insurance are critical priorities
In a world of ever-increasing cybersecurity threats, compliance and cyber insurance are two sides of the same coin. Maintaining compliance with legal and regulatory standards is preventative: it improves risk preparedness, demonstrates to business partners that your business takes security seriously, and (in the case of data privacy laws) prevents costly fines. Meanwhile, investing in cyber insurance ensures that if a breach does occur, your business is prepared to manage any fallout.
Passing compliance audits and securing favorable cyber insurance terms require many of the same things; an insurance cybersecurity assessment asks many of the same questions as a SOC 2 audit.
This includes questions like:
- How does your organization enforce role-based access controls (RBAC)?
- What mechanisms are in place to enforce multi-factor authentication (MFA)?
- How do you manage authentication for third-party vendors or contractors?
The problem is that all these questions are impossible to answer if you have unmanaged devices and applications accessing company data, since you have no way of ensuring that they are updated and secure.
In the past, it was possible to pass an audit or purchase a cyber policy without addressing these unmanaged forms of access or by declaring them “out of scope” for an audit. However, in recent years, insurance providers, data privacy laws (such as GDPR and CPRA), and voluntary compliance standards (like SOC 2 and ISO 27001) have all demanded greater accountability regarding how sensitive information is handled.
As Omdia’s report says, “Increasingly, compliance requires security leaders to control risks associated with app sprawl, secure access to sensitive data and enforce device governance standards – even on apps and devices previously considered low-risk or unmanaged."
With these stricter security requirements, maintaining compliance is becoming increasingly complex, time-consuming, and expensive. That’s why Omdia suggests that simplifying compliance is one of the most impactful goals a security leader can have.
How 1Password Extended Access Management simplifies compliance
1Password Extended Management is a security platform designed to manage the forms of access left unsecured by traditional security tools. With this platform, IT and security teams can achieve visibility and control over all devices, applications, and identities that access company data, thus fulfilling major compliance requirements.
Here are some of the ways 1Password maps to key compliance standards:
ISO 27001
- Access and Authentication: Enforce RBAC, MFA, and contextual access controls for systems and data
- Audit Trails and Monitoring: Streamlined audits with complete event logs across all 1Password products
- Encryption and Device Security: Protect credentials with AES-256 encryption; monitor endpoint health with 1Password Device Trust
SOC 2
- Security & Confidentiality: Encrypt secrets in vaults, enforce strong login policies, and enable breach detection and alerting
- Availability: Restrict access based on device compliance and integrate with IdPs to support dynamic access decisions
- Audit Readiness: Use real-time logs and contextual reporting to simplify SOC 2 audit prep
GDPR
- Data Access Controls: Enforce least privilege, RBAC, and MFA to reduce exposure to personal data
- Accountability & Transparency: Enable DSAR reporting, audit logs, and automated compliance reports
- Breach Response: Integrate audit logs and incident workflows to respond within the 72-hour GDPR window
“XAM addresses these evolving compliance requirements by unifying access governance under a single platform. It simplifies compliance reporting and audit readiness by renforcing policies aligned with standards like SOC 2, ISO 27001, and GDPR. Moreover, with insurers increasingly requiring proof of robust identity security and risk mitigation measures, 1Password Extended Access Management’s capabilities in automated policy enforcement, risk identification, and remediation provide a clear path toward meeting these expectations and securing favorable cyber insurance terms.” - Omdia.

 by Elaine Atwell on
by Elaine Atwell on