Omdia, a global analyst and advisory leader, recently released a report called “How Extended Access Management (XAM) closes the gaps in security.” The report defines the challenges of modern access management as:
- App sprawl: The uncontrolled proliferation of apps, including shadow IT
- Identity sprawl: The uncontrolled growth of user identities, such as employees, contractors, and AI agents
- Device sprawl: The explosion of devices accessing corporate resources, including unmanaged BYOD and contractor devices
These unmanaged forms of access create an Access-Trust Gap: The security risks posed by unfederated identities, unmanaged devices, applications, and AI-powered tools accessing company data without proper governance controls.
Omdia recommends five strategies for organizations that want to close this gap and improve security and business outcomes:
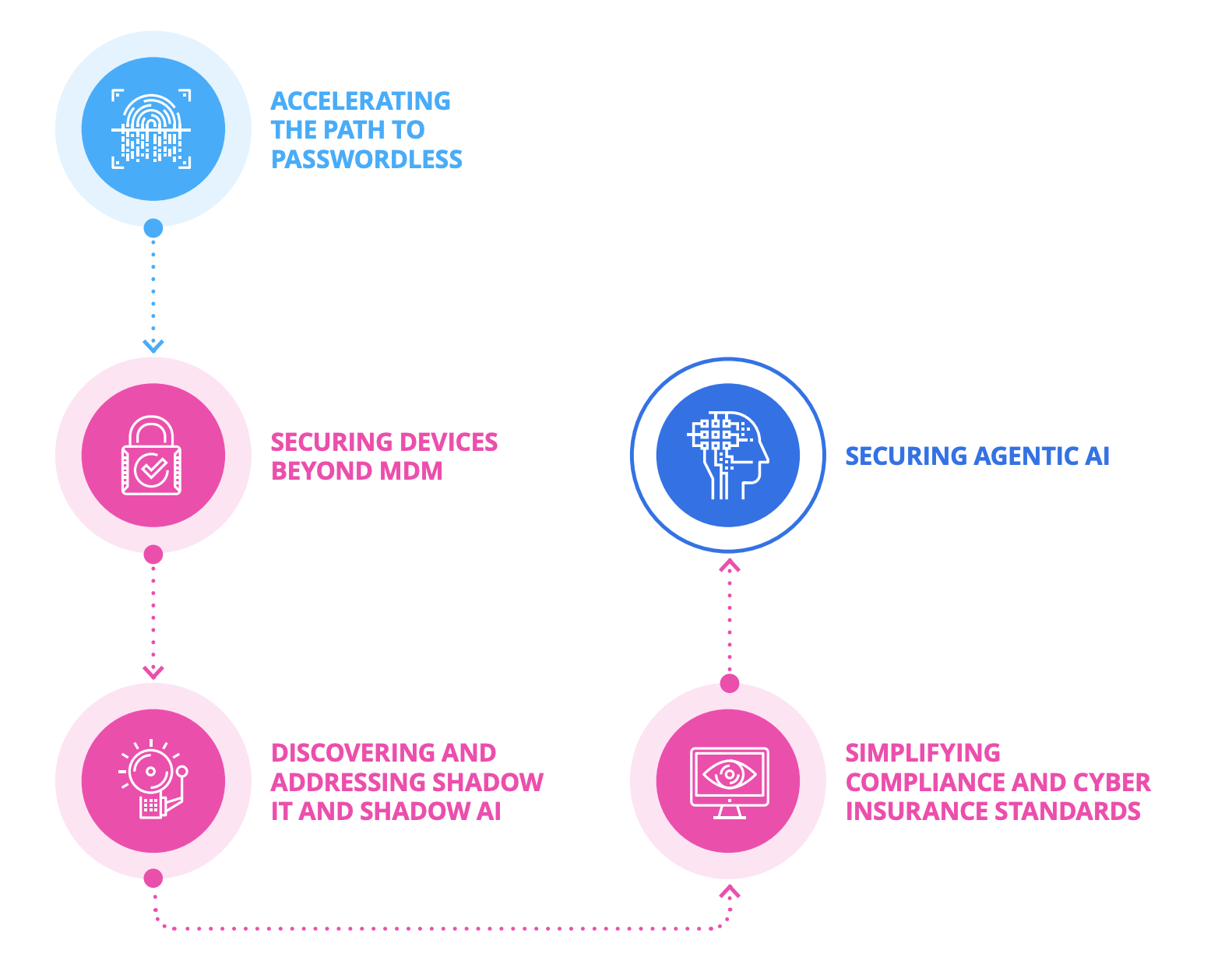
In our previous blog post in this series, we dug into the first strategy: Accelerating the path to passwordless. In this post, we’ll explore the second strategy: Securing devices beyond MDM.
Why device security must go beyond MDM
As Omdia’s report notes, “Fundamentally, security and IT teams have a mandate to ensure that only trusted devices can access their resources.” Fulfilling this mandate is critically important since untrusted devices are at a higher risk of malware infections, can download sensitive data or unsanctioned shadow IT, and – in the worst-case scenario – may belong to a bad actor.
The go-to tools for providing endpoint security are mobile device management (MDM) solutions. IT teams use MDMs to remotely enforce baseline compliance on so-called “managed” devices – usually company-owned laptops and phones. MDMs are undeniably useful, especially for their ability to remotely lock and wipe devices, but they have serious limitations.
“MDM coverage often stops short of the full picture, leaving personal devices, contractor laptops, and unmanaged endpoints outside the purview of IT. According to Microsoft’s Digital Defense Report, published in December 2024, 92% of successful ransomware attacks involve unmanaged devices. There is a clear need to discover and secure all the devices used for work, not just the IT-managed and company-provided devices that are secured by today’s typical cyber tech stack.” - Omdia, How Extended Access Management (XAM) closes the gaps in security
We explored the strengths and weaknesses of MDMs at length in our ebook: Why MDM isn’t enough for device security. The ebook highlights several areas where MDM solutions are problematic. In addition to the most glaring problem of “unmanaged devices,” most MDMs provide only a skin-deep version of compliance based on just a handful of device properties. On top of that, MDMs can be disruptive and frustrating for end-users since they often rely on forced restarts and other blunt-force tools to enforce compliance.
With that in mind, IT and security leaders must find an endpoint security solution that:
- Secures devices that MDM doesn’t manage.
- Provides more robust security checks than MDM for both managed and unmanaged devices.
- Prevents unknown and unhealthy devices from accessing corporate resources.
- And finally, accomplishes all this without harming employee productivity or morale.
How 1Password Extended Access Management secures devices beyond MDM
1Password Extended Access Management addresses MDM’s shortcomings through 1Password Device Trust. This solution ensures that only known and secure devices can authenticate to a company’s apps, using one of two mechanisms. Device Trust Connect works by integrating with a company’s IdP, such as Okta or Microsoft Entra. Meanwhile, Extended Device Compliance works by integrating with 1Password’s Enterprise Password Manager Browser Extension.
Omdia’s report describes how it works:
“Before access is granted to a SaaS application, 1Password can validate a device’s encryption status, ensure that security software is installed and running, and verify compliance with organizational security standards. This ensures that any device trying to connect to an organization’s apps is healthy and belongs to a known user. Devices that fail these checks are prevented from authenticating until the issue is remediated – either automatically or with step-by-step user guidance.” - Omdia, How Extended Access Management (XAM) closes the gaps in security
Unlike MDM, 1Password Device Trust is compatible with BYOD and contractor devices. Device Trust’s privacy-centric approach and inability to remotely wipe or lock devices makes workers comfortable with its presence on their personal phones and laptops. 1Password Device Trust also allows admins to enforce compliance based on hundreds of device properties, enabling a much more fine-tuned approach to endpoint security than MDM can provide.
1Password Extended Access Management can finally bring every approved device into the fold, and effectively lock out untrusted devices.
As Omdia’s report concludes:
“Omdia believes that [1Password’s] approach transforms the endpoint from a weak link into a controlled and trusted access point, reducing the risk of malware, ransomware, and unauthorized data access.”

 by Elaine Atwell on
by Elaine Atwell on