For companies looking to get their data practices in order, the ISO 2700 standards provide a valuable starting point to use when crafting policy.
The Wild West era of data privacy and cybersecurity is coming to an end. The public has soured on companies (including Big Tech) that scooped up their personal data and then failed to protect it from breaches, hacks, and their own worst impulses. And companies themselves have come to see that no industry is safe, as hackers hold hospitals for ransom and paralyze the operations of everything from airlines to casinos.
If we were in a Western movie, this would be the part where the townsfolk pray for a Sheriff to show up and restore order, or at least come up with some rules that everyone can agree to follow. And at present, the most comprehensive set of rules is the ISO/IEC 27000 series of standards.
What is the ISO/IEC 27000 family of standards?
The ISO 27000 series is a collection of best practices for how organizations can manage information security by creating, maintaining, and evaluating an Information Security Management System (ISMS).
This international framework is respected for its rigorousness and applicability across industries, and is valuable to any organization seeking to improve its information security risk management and become compliant with data privacy laws such as GDPR.
The standards in the 27000 series provide detailed guidance on various aspects of information security. Some standards are technical, some deal with governance and organizational risk management, some are industry specific, and others are directed at auditors. But the uncontested centerpiece of the 27000 series is ISO 27001, the only standard for which it’s possible to be certified.
The 27000 series come to us from two global standards bodies: the International Electrotechnical Commission (IEC) and the International Organization for Standardization (ISO)1. Its members meet regularly with experts to revise existing standards and add new ones. Recent additions include ISO 27403, which concerns IoT, and a revision of ISO 27031 concerning cybersecurity readiness for business continuity.
(Note: even though the full name of all these standards is ISO/IEC, going forward, we’ll mostly stick with the more commonly-used “ISO.")
An overview of the ISO 27000 standards
It would be prohibitively time consuming to read every standard within this family, but it’s worth getting a general sense of what they contain, so you can focus on the ones that apply to you.
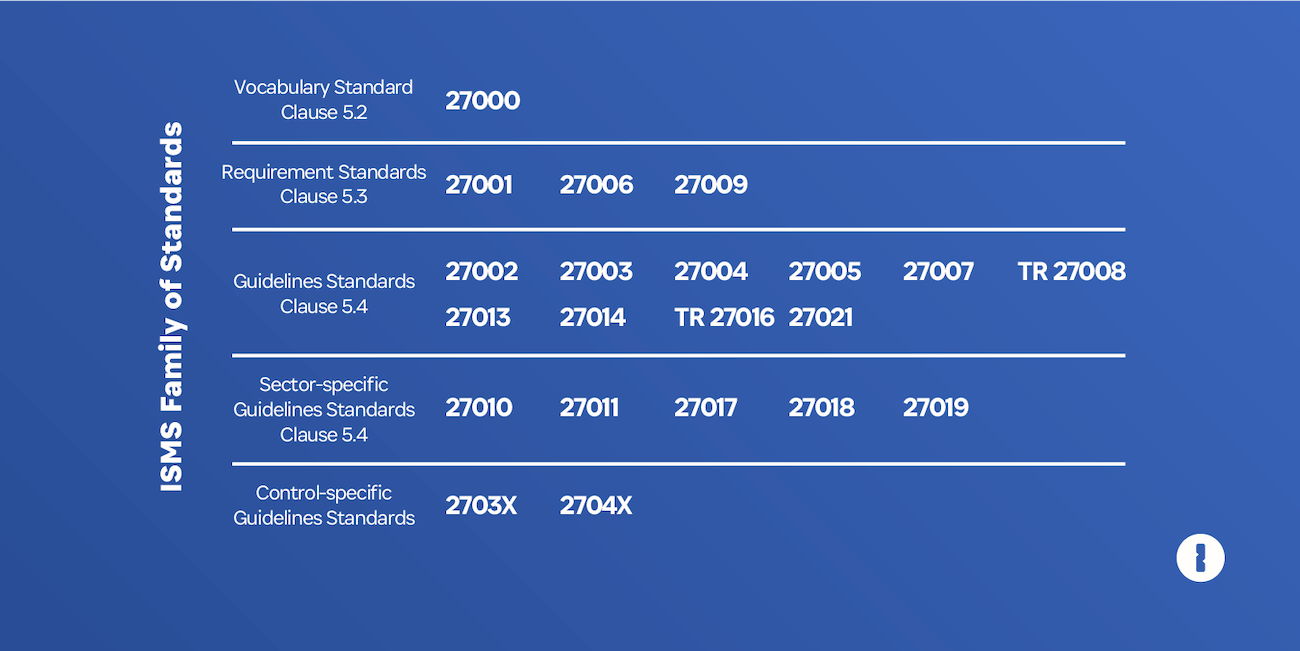
ISO 27000 introduces the series by defining key vocabulary terms and providing an overview of the other standards. It categorizes the series as follows:
Standards describing requirements
Standards describing general guidelines
Standards describing sector-specific guidelines
Control-specific guidelines
Standards describing requirements
ISO 27001
When people talk about ISO 27000 compliance and certification, they really mean this one. Broadly, it defines the requirements for an ISMS. Organizations that meet these requirements can receive certification.
This standard covers 14 domains that touch on data security and 114 controls for how an ISMS should manage each. For instance, Annex A.8 deals with asset management, and its controls include making an asset inventory, documenting an acceptable use policy, and logging any non-returned asset as a security incident.
There are three pillars to ISO 27001, and every other standard in the family reinforces them:
Documentation: All data security policies must be clearly documented, and that documentation must be accessible to all relevant stakeholders.
Accountability: ISO 27001 auditors expect to see buy-in to the ISMS at every level of the organization–participation from leadership, clear definitions for who is responsible for each organizational risk and its remediation, and a workforce that is aware of and compliant with all policies.
Continuous assessment and improvement: Achieving and maintaining ISO 27001 compliance requires ongoing internal and external audits, regular risk assessment and documentation updates, and employee training.
Getting ISO 27001 certified requires a significant investment and is usually reserved for companies with high-risk data and international deals. Because of this there’s generally a generous enough window to meet updated guidelines. For instance, the latest update to the standards came in 2022, and became required for compliance on April 30, 2024. Companies that were already compliant with the previous version will need to update to the new standards by October 31, 2025.
However, many organizations that forego the formal audit process still try to be as compliant as possible, to avoid data breaches and meet their legal and contractual obligations.
ISO 27006
This is one of the handful of standards intended for auditors and accreditation bodies. It lays out the requirements for anyone hoping to become an auditor.
ISO 27009
This standard deals with applying ISO 27001’s requirements in sector-specific contexts. Per the 27000 document, “It explains how to include requirements additional to those in ISO/IEC 27001, how to refine any of the ISO/IEC 27001 requirements, and how to include controls or control sets in addition to ISO/IEC 27001:2013, Annex A.”
Standards describing general guidelines
ISO 27002
ISO/IEC 27002 might be the second-most recognizable entry on this list. It works as a supplement for ISO 27001 and goes into much more detail about the purpose of each control and how to implement it. It’s representative of most of the standards in this section, which expand on security principles and get into the specifics of security techniques.
ISO 27003
This is another broadly applicable standard that deals with implementing an ISMS. It lays out the role of leadership, the planning process, and how to evaluate and improve upon performance. Per one expert, ISO 27003 is particularly useful for providing “a further page of explanation, practical guidance and real-world examples in this area. The end result is that the reader gains a _much _better understanding of the requirements from ‘27001 and a clearer idea of how to go about satisfying them.”
ISO 27004
The ISO/IEC 27004 document specifically concerns methods for monitoring and evaluating the performance of the ISMS.
ISO 27005
The facet of ISO 27001 under the microscope in ISO/IEC 27005 is risk management, and putting organizational processes for it in place.
ISO 27007
Regular internal and external audits are a key requirement of ISO 27001 compliance, and this standard offers guidance on how to conduct those audits, including the competence requirements for auditors.
ISO 27008
Another standard geared toward auditors, this one lays out how to assess compliance with information security controls.
ISO 27013
Data security isn’t the only concern when it comes to managing IT assets, and any standard must be able to coexist with other management systems. ISO 27013 describes how to integrate ISO 27001 and ISO/IEC 20000-1, which deals with general IT service management.
ISO 27014
This standard deals with governance for information security and the role of governing bodies in providing oversight on security issues.
ISO TR 27016
Assessing the risk level of information assets is one of the first steps in achieving ISO 27001 compliance. ISO TR 27016 offers a roadmap for prioritizing those assets based on their value. To quote ISO 27000, it helps organizations “to better understand economically how to more accurately value their identified information assets, value the potential risks to those information assets, appreciate the value that information protection controls deliver to these information assets, and determine the optimum level of resources to be applied in securing these information assets.”
ISO 27021
This document delineates competence requirements for ISMS professionals, which can be helpful for organizations hiring for that role, and individuals aspiring to it.
Sector-specific guidelines
ISO 27010
This standard provides best practices for information sharing between organizations. It can be useful for maintaining information security when sharing sensitive data across sectors or international borders.
ISO 27011
The first truly industry-specific standard, this one governs telecommunications organizations.
ISO 27017
This standard–first introduced in 2015–provides security controls specific to cloud computing and has recommendations for cloud services providers and customers.
ISO 27018
Here we have another cloud-specific standard, concerned with establishing controls for personally identifiable information (PII) in a public cloud environment.
ISO 27019
This standard deals with information security controls for energy utilities.
ISO 27799
Another sector-specific standard, this time for healthcare.
Control-specific guidelines
We won’t be providing an exhaustive list of these standards, but we will go over a few important and representative samples.
It’s worth noting that there are significant additions to this group of standards currently in draft form. ISO/IEC 27090, for instance, will address security threats to AI systems, and provide guidance on addressing them.
ISO/IEC 27559
This standard addresses the privacy risks of (theoretically) de-identified data, and provides guidance on thoroughly anonymizing it.
ISO 27701
This standard is classified as an “extension” to ISO 27001, which means you can actually get ISO 27701 certified as part of the ISO 27001 process. As we mentioned earlier, this standard develops a framework for privacy known as PIMS.
To quote IT Governance, it provides “much-needed guidance for complying with global privacy standards, such as the California Consumer Privacy Act (CCPA), EU GDPR (General Data Protection Regulation) and New York SHIELD Act.”
ISO 27033
This standard concerns network security and is written on a fairly technical level, suited for network administrators and security professionals.
ISO 27035
Here we have another entry that provides a how-to guide for implementing a key requirement of the ISO 27001 standard. This one is about information security incident management and includes a guide to creating an incident response plan.
ISO 27400
This entry outlines unique risks and controls for the Internet of Things (IoT).
Use the ISO 27000 standards as a roadmap for security
Before we wrap up, let’s make one thing clear: the ISO 27000 family of standards isn’t perfect. The vocabulary isn’t always consistent from one standard to the next, updates often lag behind technological and societal developments, and the naming conventions leave a great deal to be desired.
However, this series performs a valuable service by establishing international standards that security practitioners and governments alike can use to craft policy.
If you’re trying to get your data security in order, you don’t need to try to implement every control or every standard. But you can use their principles as a starting point to patch up your vulnerabilities and establish a code of practice for your organization and partners.
1Password® Extended access management’s device trust solution has helped numerous customers in their ISO 27001 certification process by providing audit-compliant endpoint security. Request a demo to see how we can help you.
You may have noticed that ISO’s full name doesn’t perfectly align with its acronym. That’s because ISO isn’t an acronym! Its founders didn’t want the organization’s name to be abbreviated differently from one language to the next, so they chose ISO (from the Greek word for equal) as the universal form. Which: very on brand. ↩︎

 by Kenny Najarro on
by Kenny Najarro on


