The Verizon Data Breach Investigations Report is to security what the Vogue September issue is to fashion: a glossy, buzzy publication that guides the industry’s conversations for an entire year.
The 2024 DBIR is no exception – it’s packed with deeply-researched insights, elaborate (and sometimes inscrutable) graphs, and its usual collection of charming footnotes. This year, the authors look at some of the biggest security headlines from the past year, such as the MOVEit hack and its aftermath, and the (surprisingly muted) impact of GenAI on breaches.
Still, if you’re a security professional or observer, a lot of the information in the 2024 DBIR will feel depressingly familiar. One fact in particular stands out: in 2024, the overwhelming majority of data breaches can still be traced to credential-based attacks and human error.

This trend has held remarkably steady in recent years. The 2020 DBIR reported that “credential theft, social attacks (i.e. phishing and business email compromise), and errors cause the majority of breaches (67% or more).” The 2022 report found that “…82% of breaches involved the human element…” while the 2023 report blames the “human element” for 74% of breaches.
This year, the “human element” accounts for 68% of breaches, which may look like a slight drop, until you consider that this year, the report’s authors are no longer including malicious insiders in this category. So that 68% is strictly the result of accidental breaches resulting from human error or victimization via phishing attacks and the like.
Likewise, it was another banner year for ransomware, with 32% of breaches involving ransomware and extortion, continuing another longtime trend.
Given how quickly cybersecurity evolves, it’s shocking to see the same ‘ol usual suspects back again. It’s like Vogue saying for five years in a row that fashion’s hottest new trend is corduroy.
When we hear about this seemingly unshakeable pattern of attacks, it can be tempting to roll our eyes or shrug our shoulders. But the appropriate reaction to these data breaches isn’t apathy, it’s astonishment.
You should find this report’s conclusions outrageous if you’re a security or IT professional who is constantly struggling to get buy-in for your programs, if you’re a worker given all the responsibility but none of the tools to protect your company, and especially if you’re an individual whose data was compromised in one of these breaches.
And you should be astonished because so many of these attacks are preventable, using security tools and training that already exist. As the Verizon 2024 Data Breach Investigations Report makes clear, the answers to our most pressing security problems are right in front of us, if we just take a close look at the data.
Credentials must be secured
Let’s start with credentials (it’s kind of our wheelhouse, after all). The 2024 DBIR found that credentials remain the number one way that attackers gain access to systems, “use of stolen credentials” is the number one initial action during breaches, and stolen credentials also account for a whopping 77% of Basic Web Application Attacks. Credentials are also a part of many other forms of data breach – credential theft is the goal of many phishing and social engineering attacks, and the first thing a bad actor will do if they gain access to an end user’s device is sniff around for unencrypted passwords on the hard drive.
For a problem this widespread, the solutions are actually pretty straightforward. Ultimately, every organization’s goal should be to move away from passwords and onto phishing-resistant forms of authentication. That means putting SSO and MFA in front of sensitive applications, and eventually retiring passwords altogether in favor of passkeys.
In the meantime, organizations can still prevent a lot of these attacks by investing in password managers for their employees. These ensure that workers create strong, unique passwords for every site, and keep them encrypted on their devices. Password managers have been around for years and are neither prohibitively expensive nor technologically complex, yet they remain underused. In 1Password’s 2022 State of Access Report, only 29% of respondents said they used a password manager at work.
So, let’s be blunt: the only way the 2025 DBIR will give us some surprising twists is if organizations start doing more to protect credentials. As the report’s author’s said in their May 1 webinar: “We’ve been beating the drum of properly protecting credentials for many years.” We’ll add our own drum kit to that cacophony in the hopes that more people start listening.
The hidden attack vector: compromised devices
The 2024 DBIR is clear about how compromised credentials threaten security. But there’s another culprit in data breaches that is just as dangerous, but gets less direct attention: employee devices.
You can think about the dangers of end user devices (by which we mean laptops, tablets, and phones) in two ways: unknown devices, and unsecure devices. Let’s tackle them in that order.
Unknown devices
An organization that allows any device to access its systems as long as it has the proper credentials is extremely vulnerable to attack. This is really an extension of the credential-based attack problem we just went over; as long as passwords remain so vulnerable to being stolen, phished, guessed, or purchased, you desperately need a stronger form of authentication. The usual advice for strengthening authentication is MFA, but even companies that implement this (and not enough do) often resort to secondary factors that are also vulnerable to phishing.
What you really need is an authentication factor that lives on the device itself and is not capable of being phished. That way, all the phished credentials in the world won’t let a bad actor authenticate on an unknown device. Making device identity a part of authentication is one aspect of a device trust solution. Now let’s look at the other.
Unsecure devices
The consequences of unsafe, unhealthy devices are all over the 2024 DBIR. Here are two examples:
System intrusion attacks, which include ransomware, represent 23% of all breaches in the 2024 DBIR. The “CIS Controls for consideration” to mitigate those attacks focus heavily on protecting devices, including maintaining firewalls on end-user devices, deploying and maintaining anti-malware software. Relatedly, the report also recommends requiring MFA for externally-exposed applications and remote network access.
Lost and stolen devices account for 199 incidents this year, 181 of which resulted in confirmed data disclosure, which presumably means those devices were improperly locked or encrypted. In this case, the “CIS Controls for consideration” include encrypting data on end-user devices, enforcing automatic device lockout, and enforcing remote wipe capability. (Unfortunately, that last recommendation may be difficult to follow for any organization with a BYOD policy, which will be unable to remotely wipe its employees’ unmanaged devices.)
So why are all these vulnerable devices accessing sensitive data in the first place? It’s partly because traditional device management solutions like MDM aren’t effective at identifying and resolving these issues. And it’s partly because so many companies let employees work on unmanaged devices that are functionally invisible to MDM.
Again, a device trust solution can mitigate these problems by ensuring that every device (even unmanaged, personal devices) is in a secure state before it authenticates.
Employee training? Anyone?
As we mentioned in the introduction, this year’s report found that 68% of breaches involved non-malicious human errors. Or, as the report’s authors put it in their webinar: “You can address two-thirds of these breaches by training and equipping your employees appropriately.”
Unfortunately, “give employees adequate training and resources” is advice that’s given and ignored as often as “use stronger passwords.” Many security vendors and practitioners would rather automate than educate, and we can all see where that approach has gotten us.
But Verizon’s data points to the ways that improved employee awareness drives improved security outcomes. Since 2016, users have gotten better at identifying and reporting phishing emails in training exercises, and that includes employees who reported after clicking the link!
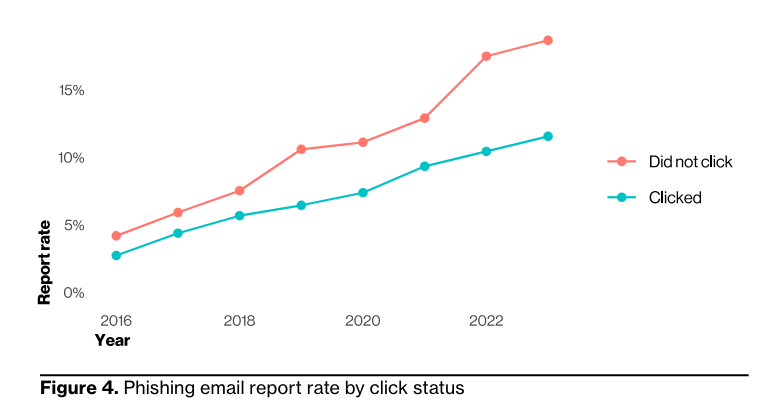
This is a great opportunity for security professionals and leaders to ask what a meaningful approach to security training and awareness programs could look like, instead of (to be brutally honest) doing the bare minimum to check a box in a compliance audit.
In our experience, the best way to make employees into security allies is to make education a part of their day-to-day experience, rather than a semi-annual distraction. Encourage and empower employees to fix problems (such as changing compromised passwords, updating software, and turning on their firewalls) themselves, and explain the reasoning behind it. You’ll soon find your workforce taking more responsibility over security, instead of thinking of it as someone else’s problem.
Let’s not do this again next year, okay?
Though many of its conclusions are all-too-familiar, 2024 DBIR should be a wake-up call for anyone who cares about cybersecurity. Unless we fix some of our foundational weaknesses, we’re in danger of succumbing to apathy. On April 24, The Information reported that companies are beginning to “lose faith in the effectiveness of cybersecurity software” since “seemingly no matter how much security software companies are buying, cyberattacks continue to get through.”
But the problem isn’t the concept of cybersecurity software – it’s that many of these solutions ignore the obvious issues that stem from weak credentials, compromised devices, and uneducated employees.
Naturally, there will always be data breaches – we’d hate to see the DBIR authors out of a job – but by addressing the fundamentals of security, we can at least start talking about some new, exciting problems this time next year.

 by Elaine Atwell on
by Elaine Atwell on