Tl;dr: The Shadow IT report, conducted in late 2023, shows that 47% of companies allow employees to access their resources on unmanaged devices, authenticating via credentials alone.
Corporate cybersecurity is at something of a turning point. Companies are very concerned about hacks and data breaches, and are throwing resources at their security teams.
In particular, companies are investing in Zero Trust, a security framework that restricts access to sensitive resources based on a user’s identity and security posture. According to Okta’s 2023 State of Zero Trust report, 61% of organizations globally have a defined Zero Trust initiative in place. That’s up from the 16% who were launching initiatives in 2019.
So, what exactly is driving this urgency? The answer lies in employee devices, human psychology, and of course, a global pandemic.
The origins of the unmanaged device problem
Let’s say you’re an engineer. Before COVID, you went to work in an office, and you used the laptop the company assigned to you–the one equipped with management software that ensured your OS was up-to-date and your firewall stayed on. If you’d brought your personal, unmanaged laptop into work, that would have felt like a deliberate breach of the rules.
Then COVID happened. Fast-forward to 2023, and you’re working from home, where you can keep your personal laptop right there on the desk next to your corporate computer. One day, there’s a data visualization app you want to try out, but you can’t do it on your managed device, so you just switch to the personal one. It’s right there! Then you need to feed the app some real data from your company, so you email or airdrop it to yourself. (You promise yourself to delete it later.)
Suddenly you realize that you can log into most of your company apps on your (cooler, faster) personal laptop. And since you’re not getting any angry emails from IT, you figure it must be okay. Soon, what started as a one-time bending of the rules becomes a full-time habit.
Meanwhile, more and more SaaS apps are accessible outside your company’s VPN (assuming it has one). You’re a responsible engineer, so you wouldn’t install the corporate VPN on your personal device; that would clearly be a rule violation. But if you just happen to forget which device you’re using, and you log into a SaaS app like you normally do, that doesn’t feel like deliberate malfeasance. Plus, you’re allowed to log in on your personal phone anyway, so what’s the problem?
These choices feel harmless on an individual level, but they have played out in countless home offices across the world. And so now we have a problem where one previously did not exist: the proliferation of unmanaged devices accessing sensitive resources.
Our research shows that, despite investing in security tools that promise total visibility, 47% of companies still permit access to unmanaged devices outside the reach of those tools.
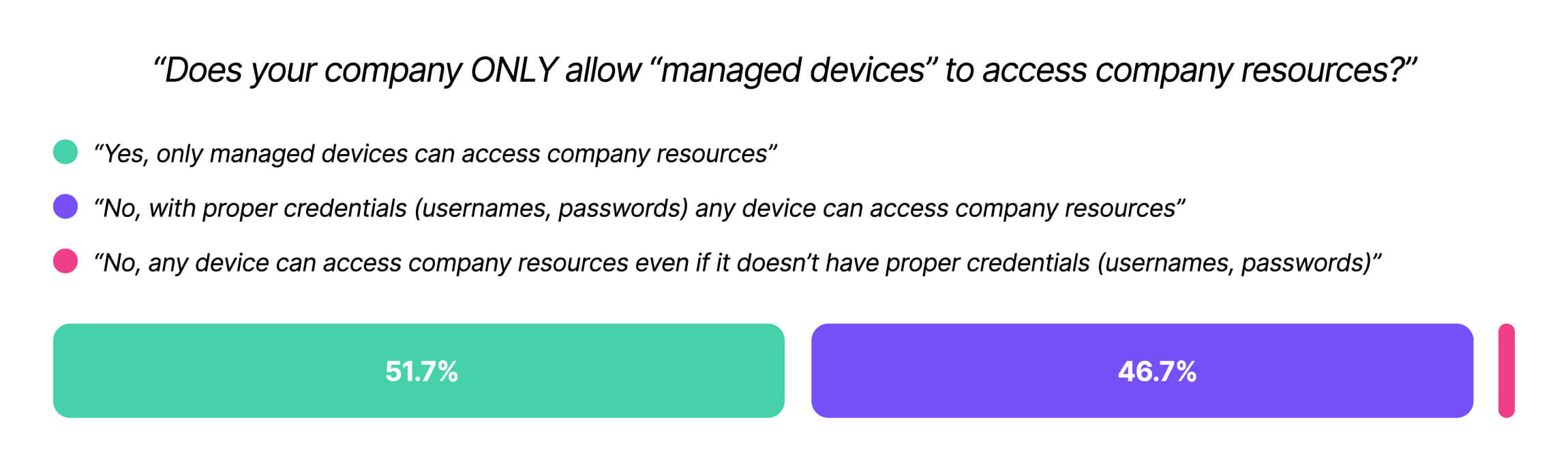
This single data point should be extremely alarming to anyone interested in security, since unmanaged and personal devices introduce a host of security concerns:
Attackers can use their own devices to impersonate employees using phished credentials.
Unmanaged devices can be compromised by malware—that’s what happened in the recent LastPass data breach.
Employees on unmanaged devices can use unapproved tools that would be detected and blocked on a managed device–for example, AI-powered browser extensions that siphon up sensitive data.
All these vulnerabilities fall under the umbrella term of shadow IT: hardware and software that is not visible to or capable of being managed by an organization.
Let’s make it clear: Unmanaged devices are shadow IT, and shadow IT is incompatible with a successful Zero Trust architecture.
Google’s famous BeyondCorp initiative—widely credited with kickstarting Zero Trust security — plainly states that “only managed devices can access corporate applications.” Yet this research reveals that unmanaged and potentially unsecure devices access sensitive resources on a massive scale.
What are unmanaged devices?
First, let’s establish what an “unmanaged” device is. NIST defines the term as: “A device inside the assessment boundary that is either unauthorized or, if authorized, not assigned to a person to administer.” In simpler terms, an unmanaged device is not subject to centralized control from an IT or security team.
Managed devices, by contrast, are equipped with software — typically a mobile device management (MDM) solution — that allows administrators to dictate what a user can do, mandate what software can and can’t be installed, and remotely wipe devices.
So why are unmanaged devices able to access company resources? There are a few general situations in which admins either allow this type of access or are unable to stop it:
Employees working on their personal computers used as part of a BYOD policy
Employees accessing company applications–often email, Slack, and other messaging tools–on their personal mobile devices
Devices outside the scope of existing management solutions, such as Linux endpoints, which are incompatible with MDMs
Third-party contractors and vendors not subject to centralized management
Unknown devices, which could be an employee logging in on a friend’s computer or in a public library, or a threat actor logging in with stolen employee credentials
Security-minded organizations try to minimize the risks of unmanaged devices by assigning company-issued laptops to employees instead of going the BYOD route and by implementing MFA to make it harder for attackers to log in on unknown devices.
Despite that, unmanaged devices creep in, whether through Linux users, contractors, mobile devices, or executives who opt out of centralized management. That last problem is more prevalent than you might assume. Our data shows that the higher you go in the org chart, the more likely you are to find people working on their personal devices.
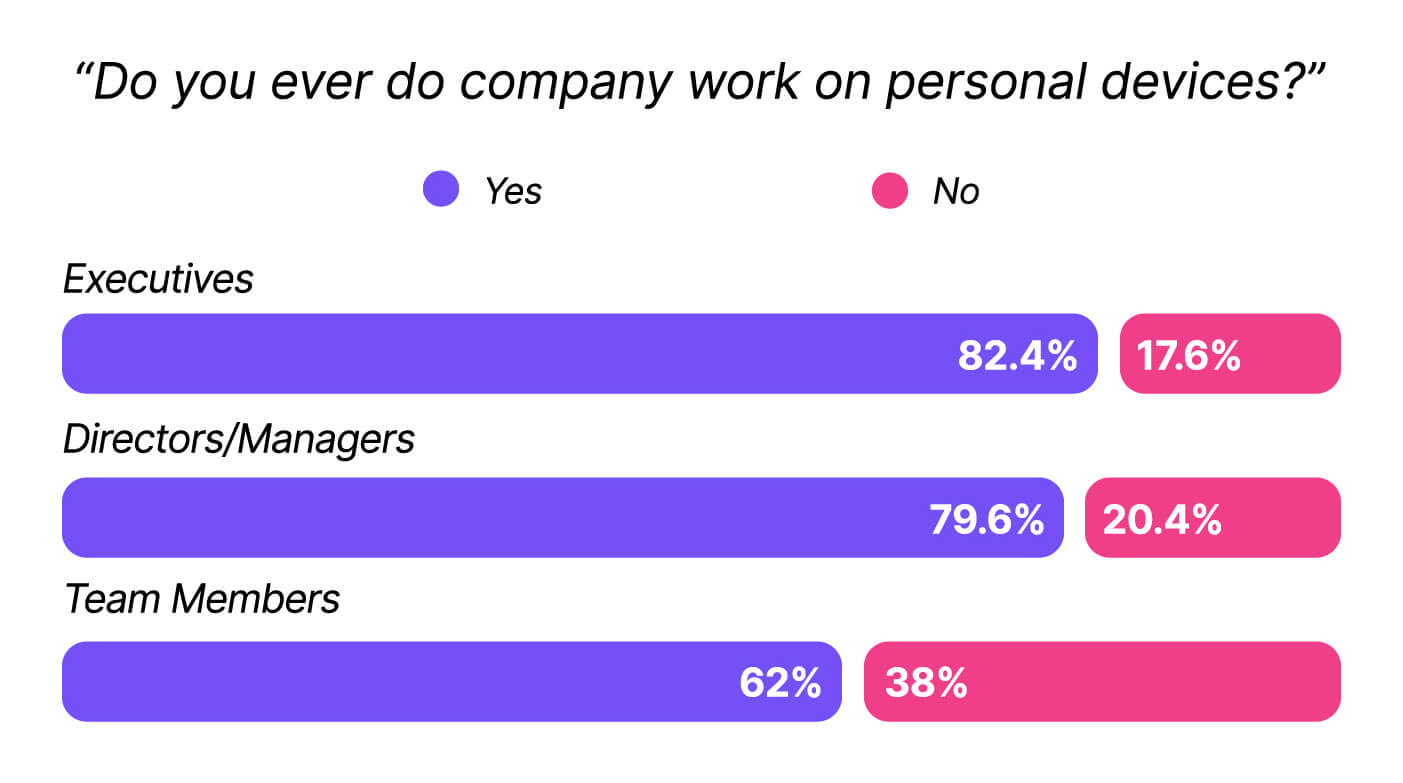
In fact, one consistent thread in this research was that executives and security practitioners engage in some of the riskiest behaviors of everyone we surveyed.
The security risks of unmanaged devices
When we asked what types of work people were doing on their personal devices, the most common answers were “email” and “collaboration tools.” That’s not surprising, since those are the applications most likely to be on mobile devices, and companies are understandably reluctant to install invasive security software on their workers' personal phones.
That being said, it’s a mistake to assume that these applications are “low-risk” just because the behavior is commonplace. There’s plenty of sensitive information in email and Slack, and they can give an attacker a foothold into a network.
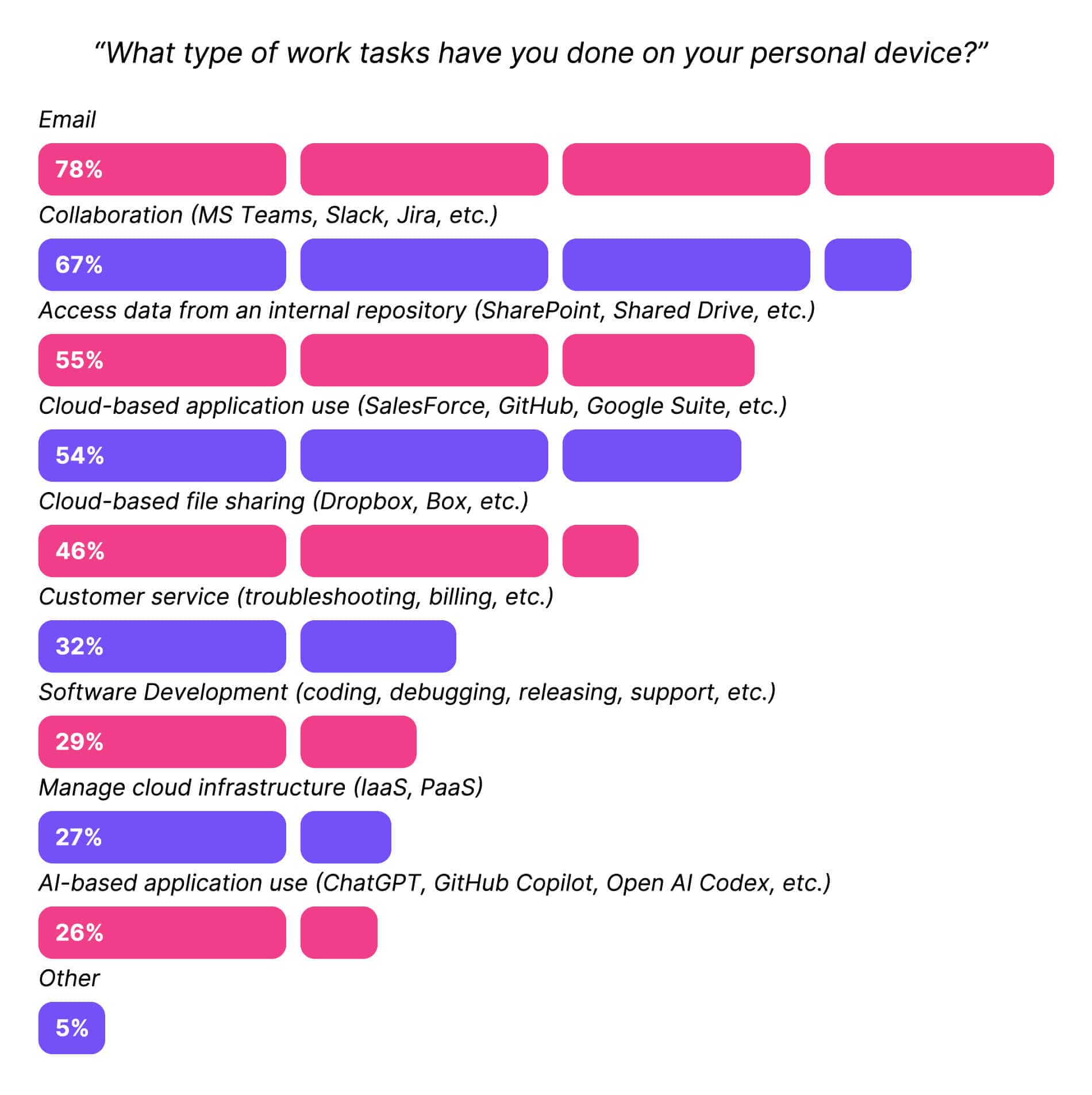
But employees aren’t just checking their email on their cell phones; they’re doing real work on real computers.
That becomes clear when we separate this data by role. 49% of developers report doing software development on personal devices, and 35% of security professionals use personal devices to manage cloud infrastructure. It’s safe to assume that this type of work isn’t happening on phones.
To quote the report:
“This is where security risks start to skyrocket. A bad actor can use a security flaw in an unmanaged device to break into the production environment, as in the LastPass breach. Even a simple smash-and-grab of a laptop can turn into a nightmare if that laptop is full of PII, and IT has no way to remotely wipe it.”
Lest we forget, a compromised device has a wealth of information right on its hard drive. We already know from our Sensitive Data report that employees download sensitive data onto their devices at 83% of companies, and only 38% have a policy prohibiting employees from storing plain-text access credentials on their devices.
Why employees use personal devices
We’ve established that unmanaged devices are inherently risky, so we wanted to understand why workers chose to use their non company-issued devices anyway. The answers ran the gamut, but three of the top six reasons related to avoiding security requirements. (That’s another data point that shows the overlap between personal and unmanaged devices, since getting around security wouldn’t be possible on a managed device.)
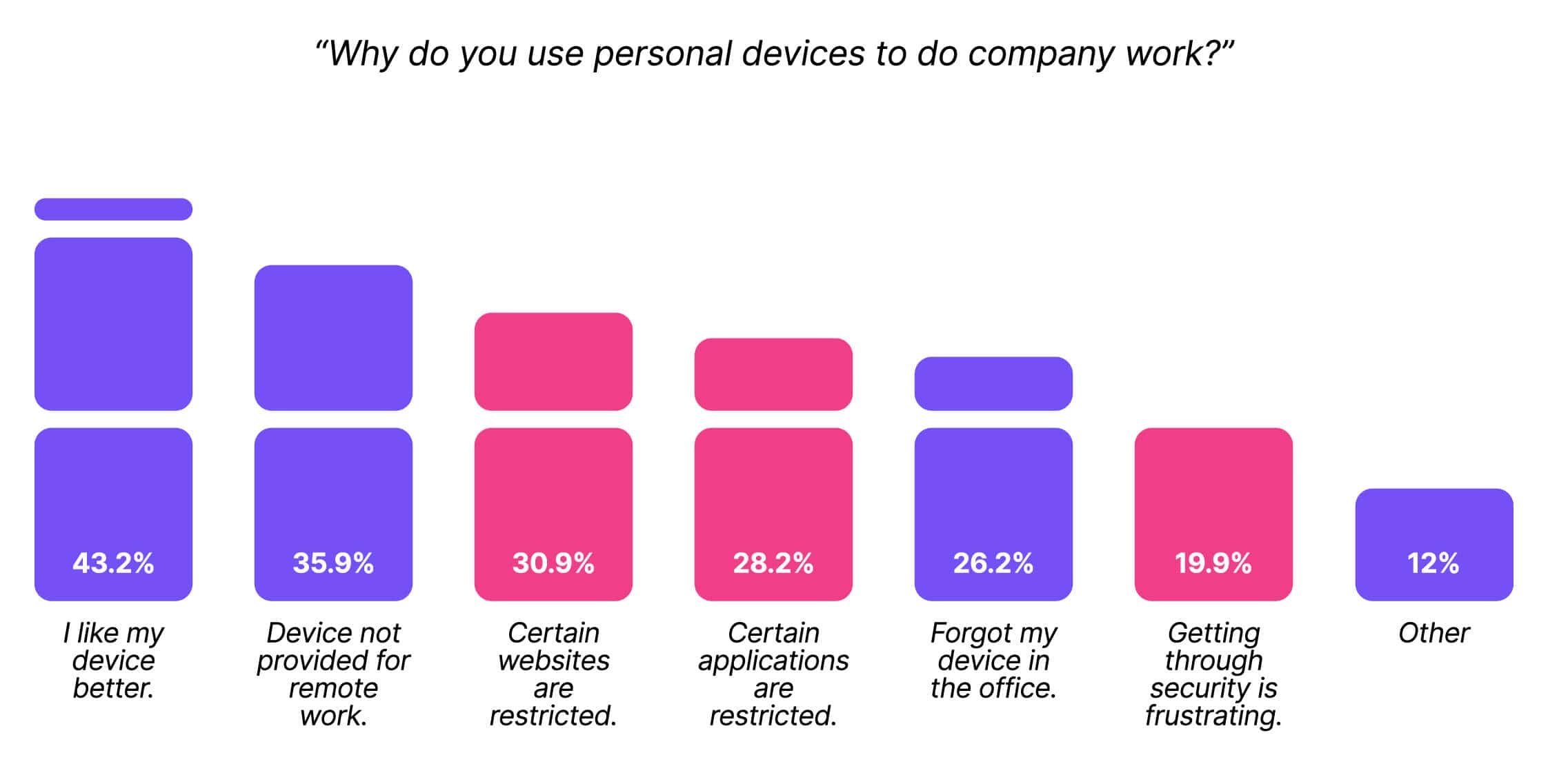
Ironically, security professionals were the most likely to report that they used their own devices to get around security. 28% said that “Getting through all the work-related security requirements (usernames/passwords, VPN, etc.) is frustrating,” compared to just 15% of respondents in IT and 21% in business roles.
(Also, in a fun fact that didn’t make the final report, 38% of executives reported that they forgot their device in the office, compared to 28% of managers and just 15% of frontline employees.)
Download the Shadow IT Report
All the data above comes from Kolide’s Shadow IT Report.
This report examines several facets of the shadow IT problem, as well as the cultural conditions that allow it to flourish. Our findings reveal that executives, security teams, and frontline workers suffer from a lack of communication and transparency, and often make incorrect assumptions about each others' behavior.
To read the full report, click here.
About 1Password Extended Access Management
As you’ve probably guessed, we didn’t create this report just because shadow IT is an interesting topic. It’s also a problem we’re actively trying to solve.
1Password Extended Access Management comes built with our Enterprise Password Manager (EPM), along with our device trust solution. That allows it to stop unmanaged and unsecure devices from accessing your company’s cloud apps. Our device trust offering fixes many of the shortcomings with existing device authentication solutions.
It works on Linux (and Windows and Macs and Android and iOS).
It doesn’t create the kinds of productivity disruptions (like forced restarts) that lead executives to opt out of device management.
It provides a lightweight, non-intrusive form of management that end-users are comfortable putting on their mobile devices and third-party contractors are willing to install on their computers. Unlike MDM, 1Password Extended Access Management can’t remotely wipe a device, and we have a privacy center for users that explicitly lists all the data we collect and who can see it.
To learn more about 1Password Extended Access Management, keep exploring the website or reach out for a demo!
 by Elaine Atwell on
by Elaine Atwell on