Omdia, a global analyst and advisory leader, recently released a report called “How Extended Access Management (XAM) closes the gaps in security.” The report argues that existing access management approaches have failed to adequately address the risks posed by unmanaged identities, applications, and devices.
“Legacy identity access management (IAM) and mobile device management (MDM) tools have fallen short of providing security while enabling a productivity-driven and innovative workforce. These tools were designed for a world where IT controlled every application, device, and tool in use…[but] in today’s world, employees freely adopt the tools and devices they need to be the most productive, regardless of whether they are provisioned or managed by their organization.” - Omdia, How Extended Access Management (XAM) closes the gaps in security
In other words, it’s all too easy for tech-savvy workers to sign up for their own apps, work on their personal devices, and experiment with unsanctioned AI tools. These are problems existing security tools were not designed to solve, to say nothing of the technical challenges of bringing disparate legacy systems under centralized control. The result of all these unsanctioned forms of access is a growing Access-Trust Gap, characterized by the security risks posed by unfederated identities, unmanaged devices, applications, and AI-powered tools accessing company data without proper governance controls.
Omdia’s report recommends five strategies for organizations that want to close this gap and improve security and business outcomes:
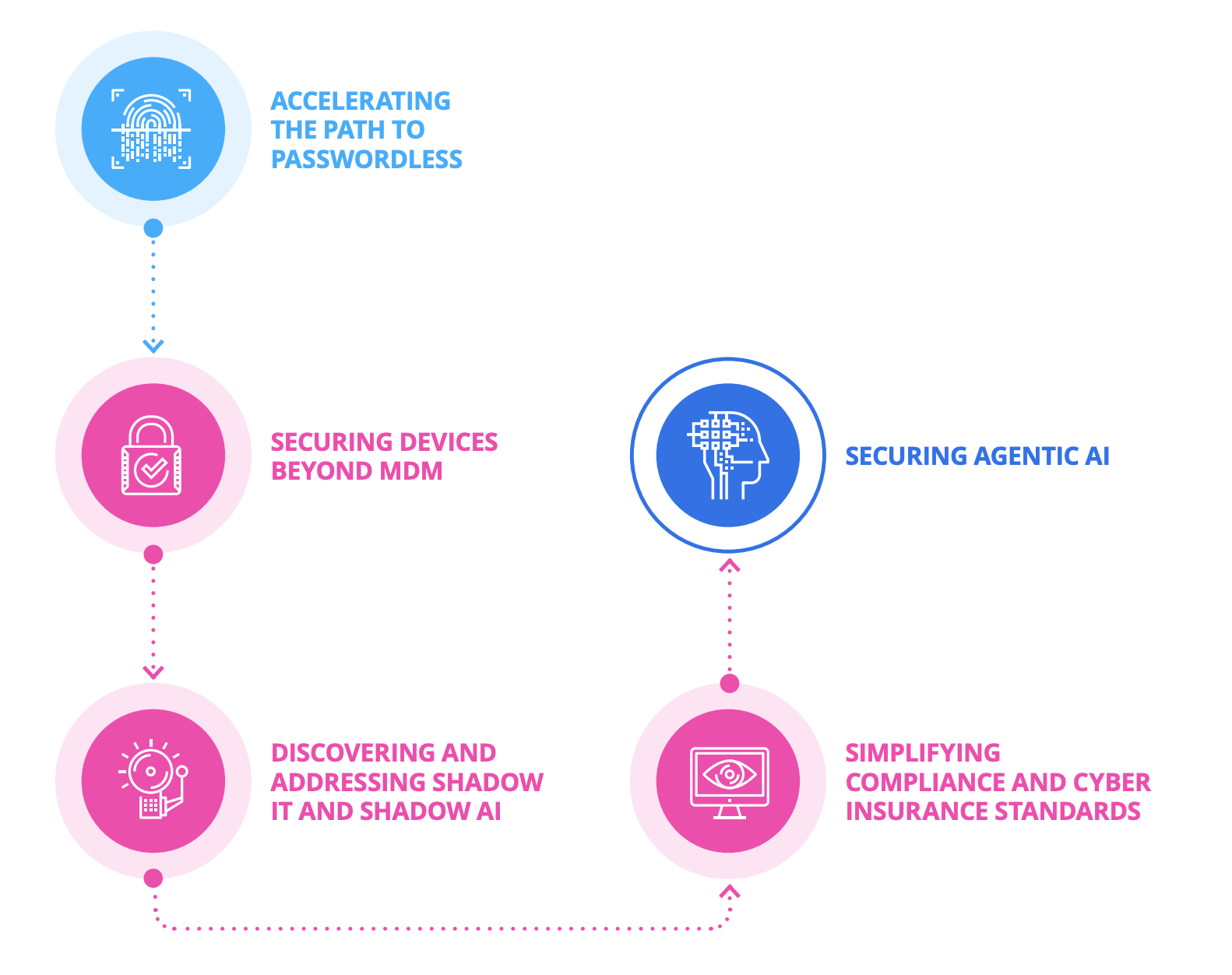
In our previous blogs in this series, we explored the first two strategies: accelerating the path to passwordless and securing devices beyond MDM. In this post, we’ll explore the third strategy: discovering and addressing shadow IT and shadow AI.
Why shadow IT and shadow AI are critical priorities
Shadow IT is a growing problem that poses a threat to security, compliance, and budgets. As the report explains:
“With the rise of SaaS and cloud-based solutions, departments often adopt their own tools without centralized oversight. This results in a fragmented SaaS environment where IT and security teams struggle to maintain visibility and control over who has access to what applications.”
This fragmented environment presents several challenges. For one thing, workers can input sensitive data into unsanctioned apps with poor security and then maintain access to said data even after their employment ends. According to Gartner, “Through 2027, organizations that fail to centrally manage SaaS life cycles will remain five times more susceptible to a cyber incident or data loss due to incomplete visibility into SaaS usage and configuration.”
Unsanctioned apps also often fall afoul of compliance standards for failing to adequately protect or preserve data. For example, in 2023, major Wall Street firms were required to pay $549 million in fines due to their employees' use of unapproved private messaging apps.
Finally, even though shadow IT is functionally invisible to IT teams, it still drains budgets. It’s difficult to know precisely how much shadow IT costs the average organization, but estimates run from about 30-50% of overall IT spending.
These were serious risks even before the explosion of generative AI tools, but shadow AI may prove to be the most dangerous subset of shadow IT. As Omdia’s report explains, “These [Shadow IT] risks are compounded by the rapid adoption of generative AI tools, often accessed without oversight and used to process sensitive or proprietary data.”
The Verizon 2025 Data Breach Investigations Report found that the use of shadow AI is rampant. They report that, of employees who regularly use GenAI, “a large number of those were either using non-corporate emails as the identifiers of their accounts (72%) or were using their corporate emails without integrated authentication systems in place (17%), most likely suggesting use outside of corporate policy.” This raises the possibility that workers are exposing data to AI tools in violation of policy, compliance standards, and data privacy laws.
Clearly, these risks demand action. To quote Omdia’s report: “Protecting organizations means securing all the apps used by employees, not just the managed apps.”
How 1Password Extended Access Management secures shadow IT
1Password Extended Management is a security platform designed to close the Access-Trust Gap, addressing both shadow IT and AI.
As Omdia’s report explains:
“1Password Extended Access Management helps organizations discover these unsanctioned tools and understand how they are accessed. It highlights high-risk applications so they can be integrated with SSO. But, it is not reliant on SSO and enables automated and secure provisioning and de-provisioning for all apps, even those not protected by SSO. This is an essential capability, given that technical limitations and the “SSO Tax” makes it unfeasible for organizations to extend SSO to every app. Additionally,1Password provides a full audit trail of access events, which is essential for responding to incidents quickly and efficiently. Further, it provides deep visibility, automation, and actionable insights, helping businesses reduce risk, streamline operations, and optimize SaaS investments.” - Omdia, How Extended Access Management (XAM) closes the gaps in security
Unlike traditional IAM solutions, 1Password Extended Access Management can discover, manage, and secure all SaaS apps and web applications, thus providing truly centralized SaaS management.
For a closer look at this solution, check out this brief video:
Omdia’s report concludes that:
“1Password Extended Access Management is certainly worth considering for organizations who are looking to go beyond legacy IAM and PAM tools to deliver universal visibility, real-time risk response, and a frictionless user experience, all of which are essential for scaling secure operations in today’s hybrid and fast-moving environment.” - Omdia, How Extended Access Management (XAM) closes the gaps in security.
 by Elaine Atwell on
by Elaine Atwell on