For years, mobile device management solutions (MDMs) have been all but ubiquitous in corporate cybersecurity. Devices enrolled in MDM are commonly referred to as “managed,” which reflects the tendency of companies to consider a device functionally secure as long as it has MDM installed.
In practice, however, MDMs lack the ability to oversee many critical aspects of device posture and security for enrolled devices. Furthermore, many devices aren’t suitable for enrollment in MDMs, leaving them unmanaged. These unmanaged devices contribute to a widening of the “Access-Trust Gap” across a company’s systems.
MDMs are a necessity for many companies, particularly for meeting compliance requirements. However they are not a complete solution for endpoint security, so in recent years many security leaders have embraced alternative or complementary solutions. Among the most prominent is a category of solutions called device trust.
Device trust solutions ensure that devices are both known and in a secure state before they can authenticate to company resources like SaaS apps. While MDM and device trust have significant differences – for example, MDM has no relationship to authentication – they both monitor and enforce device security.
For teams considering device trust as an option to replace or complement their existing MDM solution, this article will compare the relative capabilities of MDM and device trust in providing oversight and enforcement for every device in their fleet. And since 1Password offers a device trust product, (1Password® Device Trust, as part of the 1Password® Extended Access Management platform) this article will occasionally use it as an example.
Device telemetry and posture enforcement
Both MDM and device trust collect information on the security posture of devices. But there’s a stark difference in the level of detail each solution can report – and what they can do with that information.
MDM offers broad oversight
MDMs have fairly limited abilities to report on and enforce device posture, usually by acting as an admin with control over a device’s basic settings. There is some variation in those capabilities between vendors, but some of their most common abilities include:
- Restricting access to public Wi-Fi networks
- Restricting camera usage
- Requiring that a device be password protected
- Requiring that screenlock be turned on
- Forcefully installing or uninstalling apps
- App management, such as forcing app updates, allowlisting or blocklisting apps, or requiring the use of an enterprise app store
- Requiring that firewall be enabled
- Pushing out OS updates
- Enforcing disk encryption
- Remotely wiping a device in the event that it is lost, stolen, or an employee has left the company
MDMs work, in essence, by cutting the user out of the equation, forcing compliance with little regard for employee productivity or agency. In the case of OS updates, MDM remotely pushes the update to end-users and then forcibly restarts their devices to install them. This can be immensely disruptive and even lead to data loss. In the case of things like the Wi-Fi or firewall, MDM takes away the user’s ability to alter settings; if they attempt to turn off the firewall, they’ll find that the check-box has been grayed out.
Meanwhile, MDM can do very little for compliance issues that can’t be solved through blunt automation. That leaves teams with no solution for – or even awareness of – major risks to their fleet, like unencrypted SSH keys, malicious browser extensions, or the storage of sensitive corporate data on devices.
On the whole, MDM was built to provide the kind of broad oversight that was needed when it was first designed. As industry needs have evolved, some enterprise MDM solutions have attempted to achieve more granular data collection through compensatory features like extensions. In practice, such features are complex to access and manage for real-time reporting.
Device trust offers granular insights
Most device trust solutions provide insights that go beyond the limited telemetry offered by MDM.
For instance, 1Password Device Trust is based on osquery, which allows admins to query their fleets based on thousands of device properties. This lets admins have a complete device inventory with real-time insights into each device’s health and security.
For example, when a critical vulnerability is identified in a piece of commonly-used software, teams need to ensure that it’s patched. With 1Password Device Trust, admins can query their whole fleet to see which machines are running that software. Then, they can configure a Check requiring those users to install the update before they can authenticate again.
With MDM, however, admins only have insight or control over those apps that the company installed. They can’t query fleets to see who might have other vulnerable software installed. In fact, their device inventory might be split across multiple products since many of the most popular MDMs are first-party to Apple or Microsoft. Even for managed apps, admins have to forcibly restart the software for the user. This leads to more disruption to workflows and more IT tickets overall.
The ability to query across thousands of properties lets device trust solutions enforce more varied and granular policies than MDM typically can. For example, 1Password Device Trust comes with over 100 pre-built Checks based on common security and compliance concerns. On top of that, admins can write their own custom Checks tailored to their organization’s specific security needs.
This enables device trust admins to do things like:
- Identify sensitive data on a hard drive
- Ensure the timely deletion of sensitive data
- Detect unsafe browser extensions
- List Mac system extensions
- Detect the storage of plain-text credentials and SSH keys
- Require updates for OS, browsers, and other software
- Require that MDM and EDR tools are present and functioning properly
That list is only a small subset of 1Password Device Trust’s capabilities, and device trust solutions can also check for the same baseline telemetry as MDMs.
This level of granularity is possible precisely because device trust doesn’t rely on the kind of brute force enforcement used by MDM. Most device trust solutions don’t attempt to remediate issues themselves, and many rely on end-users themselves to resolve compliance issues.
Not only is this a boon for productivity (since users can install updates at a time of their choosing), it also enables device trust to function on those devices that fall outside the scope of MDM.
Mobile security for BYOD and unmanaged devices
MDM and device trust both have a lot to offer company-owned, “managed” devices. But modern companies also have to deal with the threat of unmanaged devices (those devices that aren’t enrolled in MDM). A 2023 study found that 47% of companies allowed employees to access company resources from completely unmanaged devices.
These unmanaged devices present enormous risk; they might be carrying malware, running outdated software, or belong to bad actors using stolen employee credentials. In fact, Microsoft reported that 92% of successful ransomware attacks originate from unmanaged devices.
MDM can’t secure BYOD
MDM’s capabilities are best suited to company-owned devices, where a company has a right (and even an obligation) to aggressively enforce policy. But there are many devices that fall outside that scope, and on which MDM is either impossible or inadvisable.
BYOD (bring your own device) is a common phenomenon in the modern workplace, but few organizations attempt to deploy MDM onto BYO-devices. The main reason for this is MDM’s ability to remotely lock or wipe all data from devices. This remote-wipe capability is explicitly necessary to pass many compliance audits, as it greatly reduces the risk of sensitive data being taken from stolen or lost devices, and is a major asset when securely offboarding employees.
However, on personal devices, MDM’s data wipe capabilities can be as much a compliance problem as a solution. NIST is quite clear that, “Wiping data not owned by the enterprise can cause legal issues.”
Furthermore, employees are reluctant to accept a tool that can remotely wipe (and otherwise control) a device that they own and use for their personal affairs. Attempts to deploy it can invite pushback from employees and admins alike.
Even if a company decides to deploy MDM on personal devices, it will have to contend with additional limitations enforced by MDM vendors. Microsoft Intune’s documentation specifies that “Your organization can view the location of a lost corporate-owned device. They can’t view the location of a personal device.”
MDM is also not suited for managing contractor or partner devices. In fact, it may even be impossible – a device cannot be enrolled in more than one MDM at a time, and contractor and partner devices are likely to have another MDM installed.
Finally, MDMs that can cover Linux devices are few and far between, and will often only be able to manage certain Linux distributions. Even then, Linux MDMs often have limited controls over those devices – for instance, some cannot support remote wipe for Linux.
Device trust reduces the attack surface
Device trust solutions offer a less invasive form of management that is suitable for securing personal and contractor devices. Device trust prevents noncompliant devices from authenticating to company resources without subjecting employees to forced updates and remote wipes.
1Password Device Trust places a particular emphasis on respecting user privacy and practicing transparency. The Privacy Center shows employees which device information their company can access and its potential impact on their privacy. This enables companies to securely enable BYOD without compromising either security or privacy.
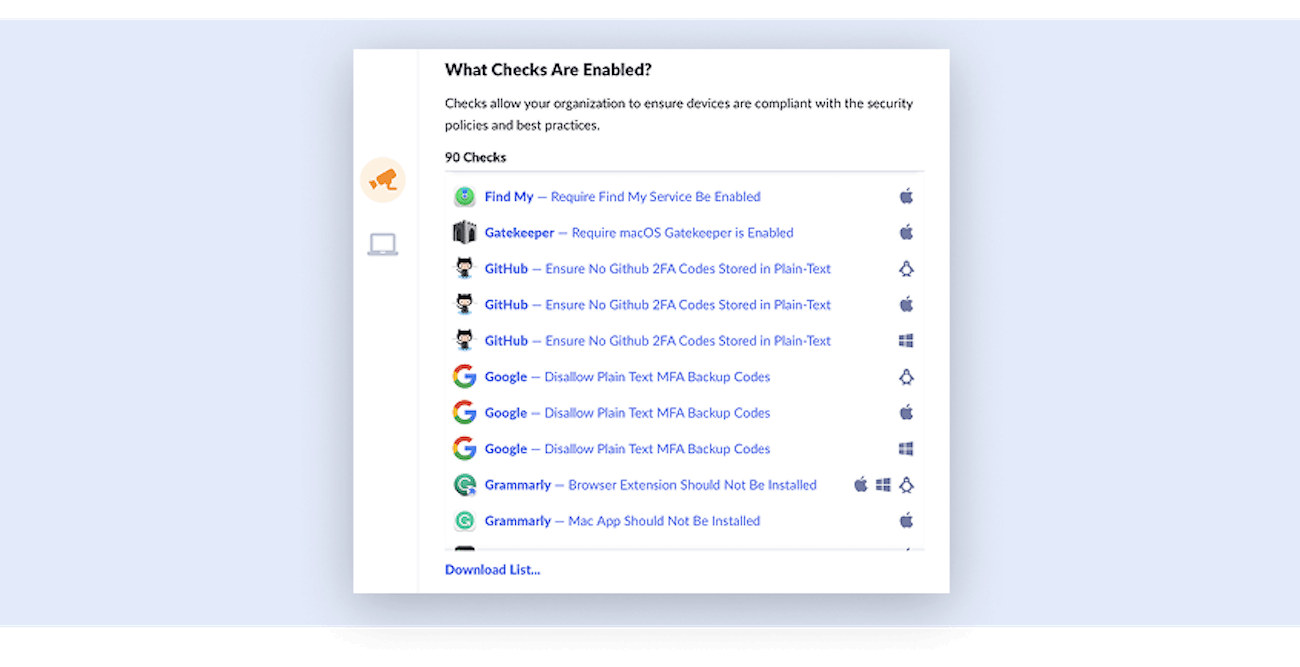
Osquery’s read-only capabilities also let 1Password Device Trust provide more comprehensive management for Linux endpoints; it offers Debian and RPM installers for Linux-based systems, and tests that all official Checks work on those devices.
Still, as popular as BYOD is, it won’t suit many organizations. For instance, BYOD is not advised for healthcare settings, where it can conflict with HIPAA guidelines.
In cases like these, device trust enables teams to ban personal devices outright. Admins can refuse registration from devices that aren’t company-owned or enrolled in MDM and block authentication from any device that isn’t registered to a user. This capability greatly reduces untrusted access, helping to close the Access-Trust Gap.
Device trust secures what MDM can’t
In recent years, an influx of new challenges have been posed by remote and hybrid workforces, such as the increasing use of personal devices in corporate environments. As these challenges have mounted, teams have struggled to compensate for the limitations of their existing MDM solutions.
Thankfully, device trust solutions are uniquely suited to address the challenges that MDM cannot. In BYOD scenarios, device trust can replace MDM, offering a secure alternative for personal devices. For company-owned devices, device trust acts as a powerful complement, strengthening security beyond MDM’s limited capabilities.
Comprehensive security requires complementary solutions. Together, MDM and device trust can offer security that’s greater than the sum of its parts.
Want to learn even more about the relative abilities and limitations of MDM and device trust solutions? Read 1Password’s complete ebook, “Why MDM isn’t enough for device security.”
 by Rachel Sudbeck on
by Rachel Sudbeck on