This article explains how, with 1Password’s Device Trust solution, you can use osquery’s file monitoring capabilities to oversee your Windows fleet.
Prior to Osquery 4.2.0, Osquery’s File Integrity Monitoring (FIM) capabilities only worked on macOS and supported versions of Linux. To fill this gap, Trail of Bits engineer @woodruffw created a new virtual table called ntfs_journal_events to finally bring basic FIM capabilities to osquery on Windows.
In this tutorial, we will take a look at how you can use 1Password’s Device Trust solution to configure and ingest ntfs_journal_events output.
What you will need
1Password’s Device Trust solution (formerly Kolide), available as part of 1Password® Extended Access Management.
A Windows 10 or 11 device enrolled in 1Password’s Device Trust solution.
Physical or remote access to the Windows device so that you can generate events to monitor.
Osquery FIM basics
The FIM in osquery is composed of two distinct pieces:
A FIM category which defines monitored paths. (eg.
C:\Users\fritz\Downloads)An events table query which populates results. (eg.
SELECT * FROM ntfs_journal_events;)
1Password’s Device Trust solution makes it easy to get up and running with the osquery FIM with minimal configuration. Let’s set up a basic FIM configuration to monitor the changes of the User’s Downloads folder on a Windows device.
To do so we will need to perform three easy steps:
Enable the osquery Options for Windows events.
Define a FIM category.
Write an
ntfs_journal_eventsquery.
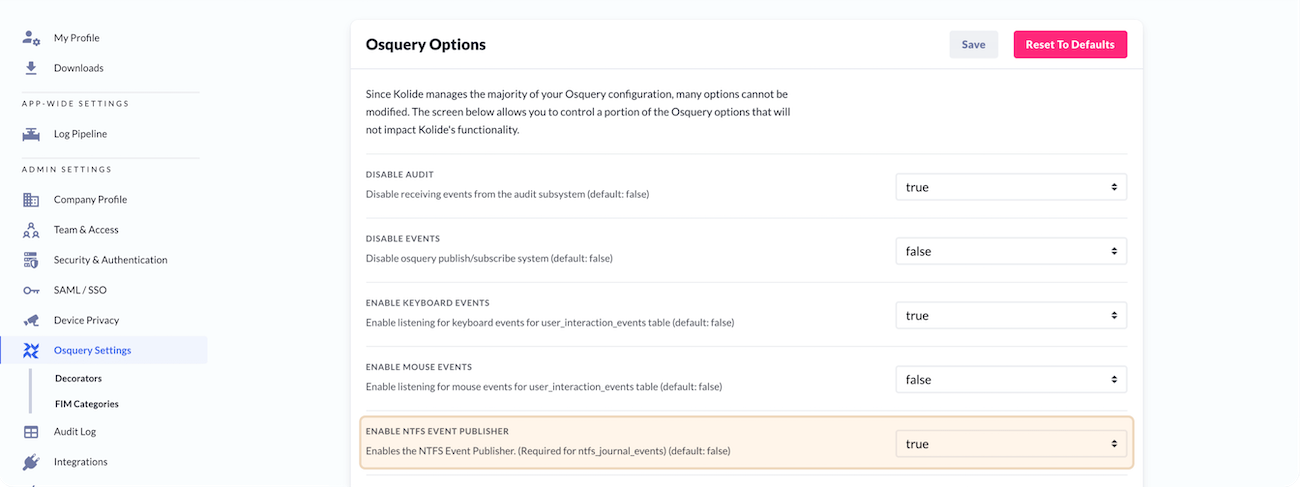
Enabling Windows events
To use the FIM, we will first need to Enable the NTFS Event Publisher by going to the “Osquery Settings” page, and setting the dropdown state to true.
Define a FIM category
Next, we will configure a FIM category. A FIM category defines a watched path, or set of paths, which will be flagged as the target of our events query.
FIM categories support the usage of wildcards, to accommodate relative paths that may be different across devices. For example, watching directories within a User directory:
C:\Users\fritz\Downloads
C:\Users\chris\Downloads
C:\Users\kevin\Downloads
All of these directories can be distilled down to a single relative path using the following wildcard approach:
C:\Users\%\Downloads
Note that a trailing slash or trailing %% wildcard should NOT be used when defining paths, or you will not recursively search subdirectories.
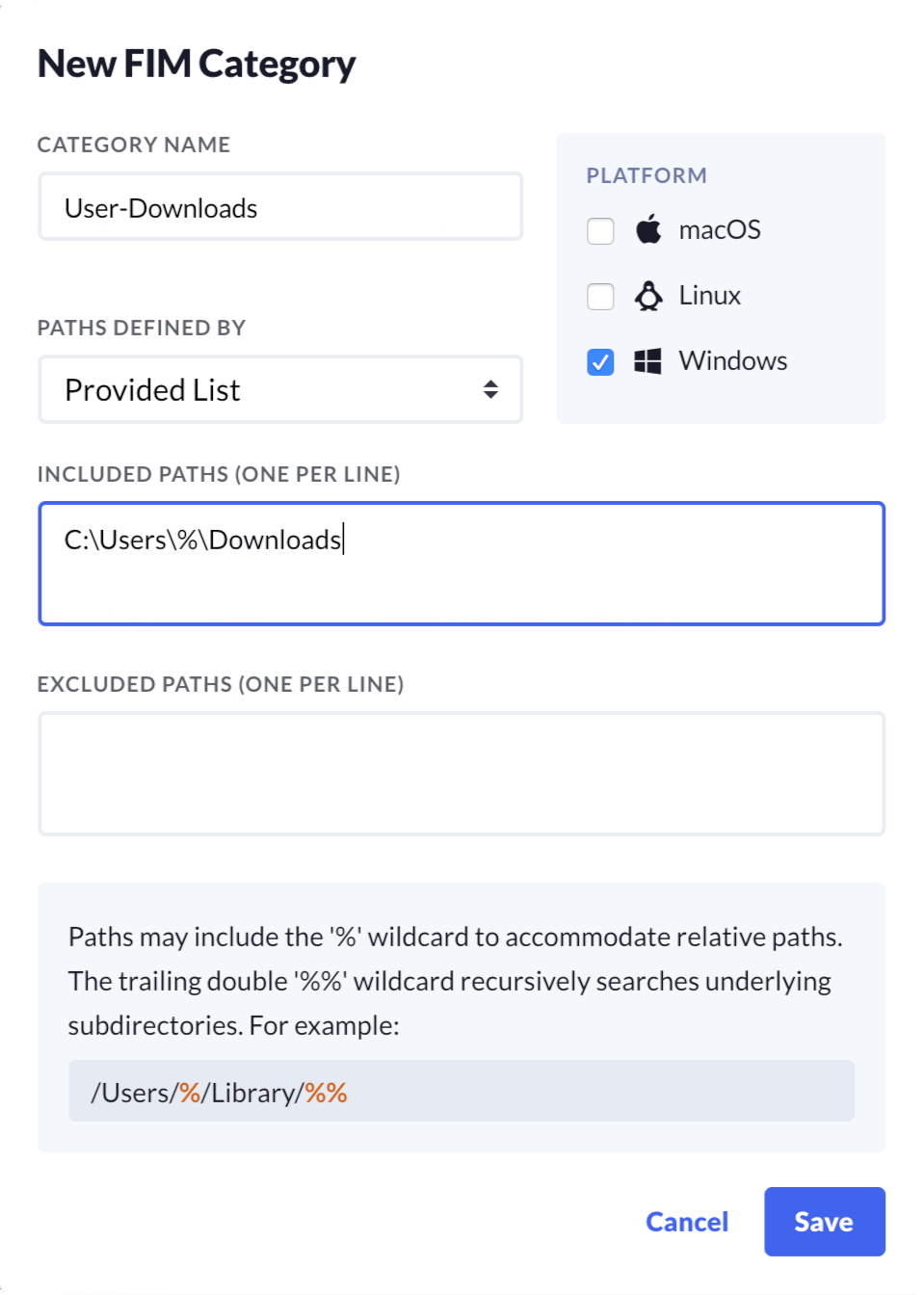
We can create a new FIM Category by navigating to: “Osquery Settings/FIM Categories,” and then clicking on the “Add New FIM Category” button. We can then name our category and define its watched paths.
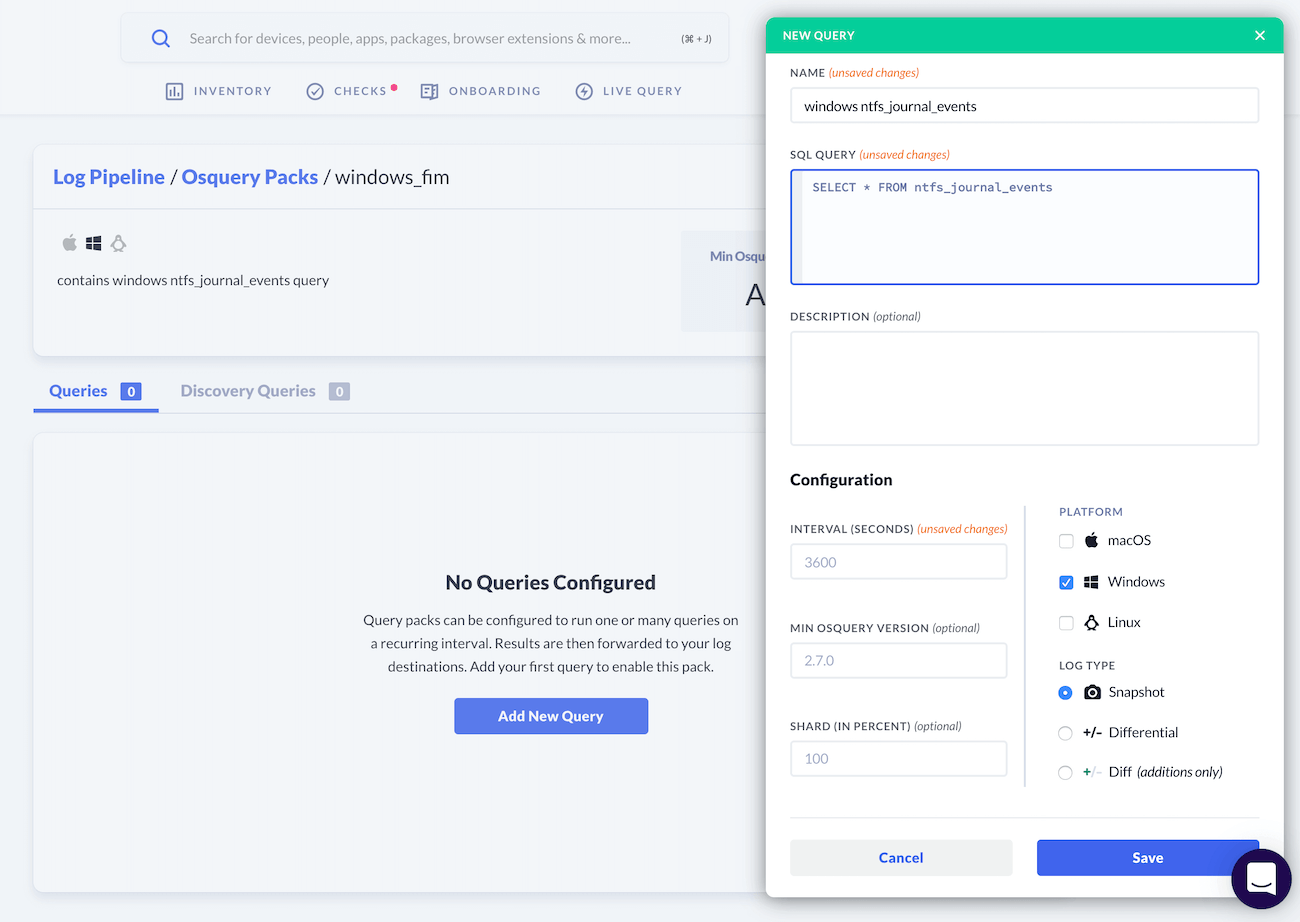
Write an ntfs_journal_events query
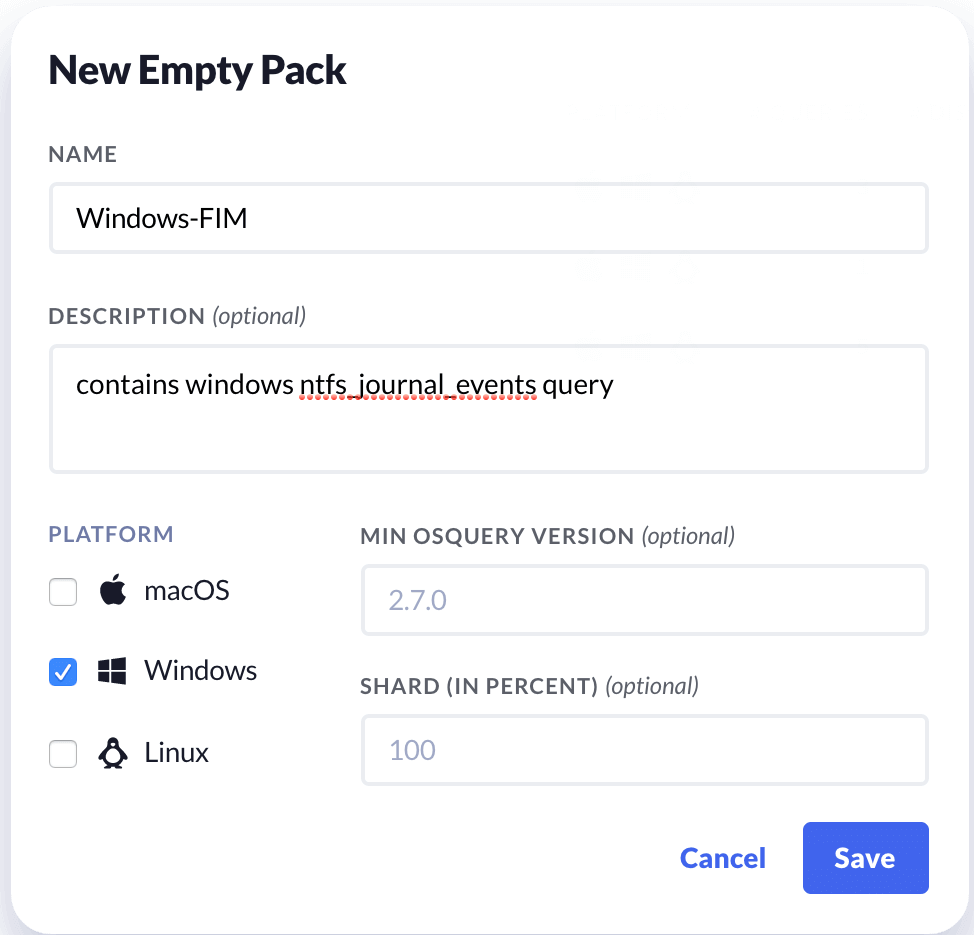
The last piece needed before we can start emitting data is a valid osquery SQL query to populate results. We will need this query to run on a recurring schedule, which we can configure by including it in an osquery Query Pack.
Create a new Query Pack by going to: “Log Pipeline/Osquery Packs”.
Click the button: “Add Pack > New Empty Pack”.
Name your pack and select Windows as the Platform.
Once we’ve created our Query Pack, we can add our query to it:
Within the new pack, click the button labeled “Add New Query”.
Type a name for your query.
Add the following query:
SELECT * FROM ntfs_journal_events;.Select “Windows” for the platform.
Configure an interval (3600 is the default, which is every hour, but we suggest choosing a shorter interval like 10s in the beginning, so that you can verify everything is working.)
Choose “Diff” (additions only) as the log type. (Evented tables in osquery are different from other tables in that diff removals and snapshot results are not semantically meaningful.)
Click “Save”.
Viewing results of your FIM configuration
Now that you have your new FIM configuration setup, you can test it by downloading some files to your test Windows device. If you set a frequent interval for your ntfs_journal_events query, you should start seeing results quickly once you perform any actions that trigger the FIM.
Results can be previewed in the “Live Log Viewer.” This viewer listens for all logs emitted by the queries in your pack schedule, allows you to preview the output of your configured Query Packs, and confirms that osquery is emitting the desired output.
Let’s take a look at what we’ve got so far by renaming and changing the contents of a file:
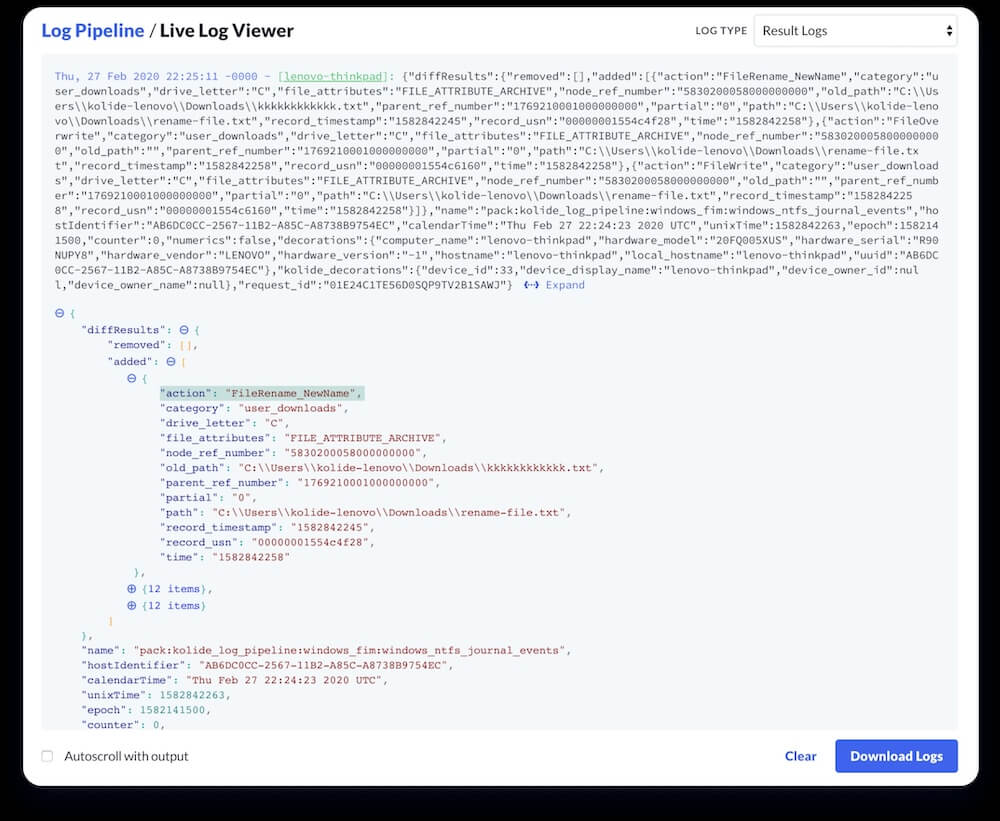
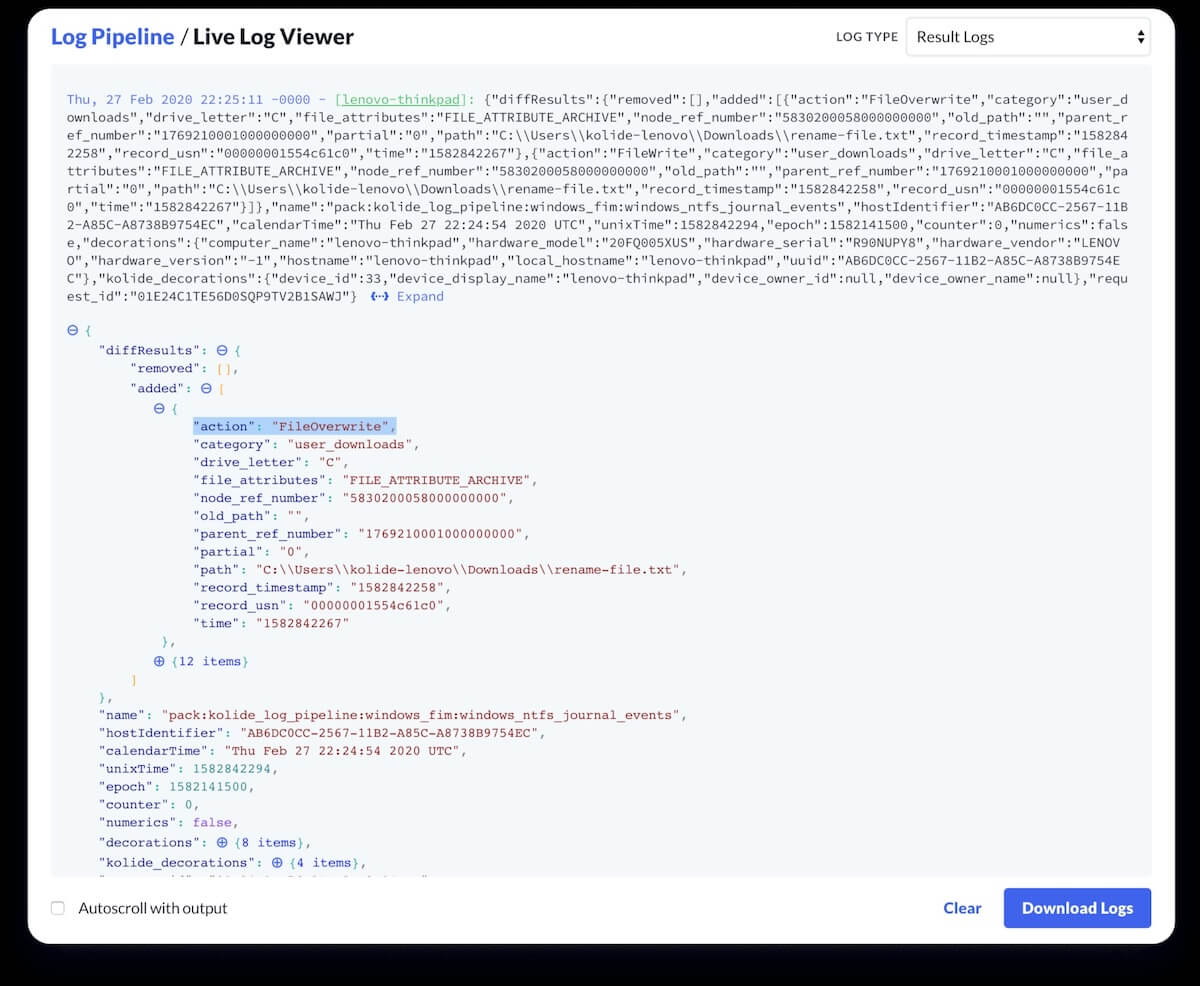
As we can see, we have two actions recorded by osquery: a FileRename_NewName and a FileOverwrite.
Setting a log destination
Now that we’ve generated useful logs, 1Password’s Device Trust solution enables you to forward them to any valid log destinations. For more information on supported Log Destinations and how to configure them, please refer to our help documentation.
Nuances to be aware of
There are a couple of items to consider while configuring your FIM ingestion rules.
Wildcard behavior
Since the FIM supports file GLOBs, you may be tempted to specify something like C:\Users\%\Downloads\%% in your FIM category. This doesn’t cause errors, but specifying this way – in-lieu of monitoring the directory itself – may result in unexpected behavior, like the following:
The osquery agent retrieves the FIM configuration.
It recursively searches paths specified by the FIM category (eg.
C:\Users\%\Downloads\%%).It registers each file found via that pattern to be watched for changes.
This means that files created after FIM configuration retrieval (during which, files are registered to be watched) will be ignored by the FIM.
Further reading & resources
Get started using the Windows FIM in osquery today
1Password’s Device Trust solution is the easiest to use and most advanced osquery fleet manager available today.
Want to learn more about how osquery can help keep your fleet secure? Learn more on the 1Password blog.
 by Fritz Ifert-Miller on
by Fritz Ifert-Miller on