This blog post describes the process for securely updating 1Password’s Device Trust agent.
From a user’s perspective, the agent update process for 1Password Device Trust is functionally invisible. Most users are familiar with having to download new updates for software, or at least having to click “yes” on a prompt to restart an app so that it can update. But the Device Trust agent doesn’t require any action from the user to update – it securely autoupdates itself and its components.
Given device trust’s importance as a security tool and its role in user authentication, it’s really important that the autoupdate process be as secure as possible. So let’s explain why we chose this approach, and how we ensure that our process is secure.
How and why do we autoupdate the Device Trust agent?
The 1Password Device Trust agent autoupdates itself in order to receive new features, improvements, and fixes as quickly as possible.
At a high level, these are the steps in the autoupdate process:
Once an hour while the device is awake, the agent checks for updates (both for itself and for the osquery binary).
If an update is available, the agent downloads and verifies the update, stores it in its update library, and runs the update.
Whenever the device is restarted, the agent chooses the appropriate update from its update library to run.
The details
To ensure that updates have not been tampered with, we use The Update Framework (TUF) to verify signatures. TUF defines a specification for secure software update systems.
What is TUF and why do we use it?
The Update Framework (TUF) is the framework that we use for providing secure software updates to the 1Password Device Trust agent. TUF computes metadata about each update (called a “target file” in TUF), and then stores that metadata in a new, signed version of its metadata files, creating a trusted line of continuity from the first version of these files to the latest. This trusted line of continuity allows the 1Password Device Trust agent to safely download updates, to confirm the integrity of the updates, and to be certain that it is running the latest update available.
How does the 1Password Device Trust agent make updates available using TUF?
We use TUF to serve the checksum and file integrity information for agent updates. We also store which update is the current stable version in TUF. We store this data in a bucket (the “TUF metadata bucket” in the diagram below), and the binaries in a separate bucket (the “Updates bucket” in the diagram below).
Per the TUF specification, we encrypt and store the signing keys separately from the 1Password Device Trust agent updates and the TUF metadata, in a secret manager.
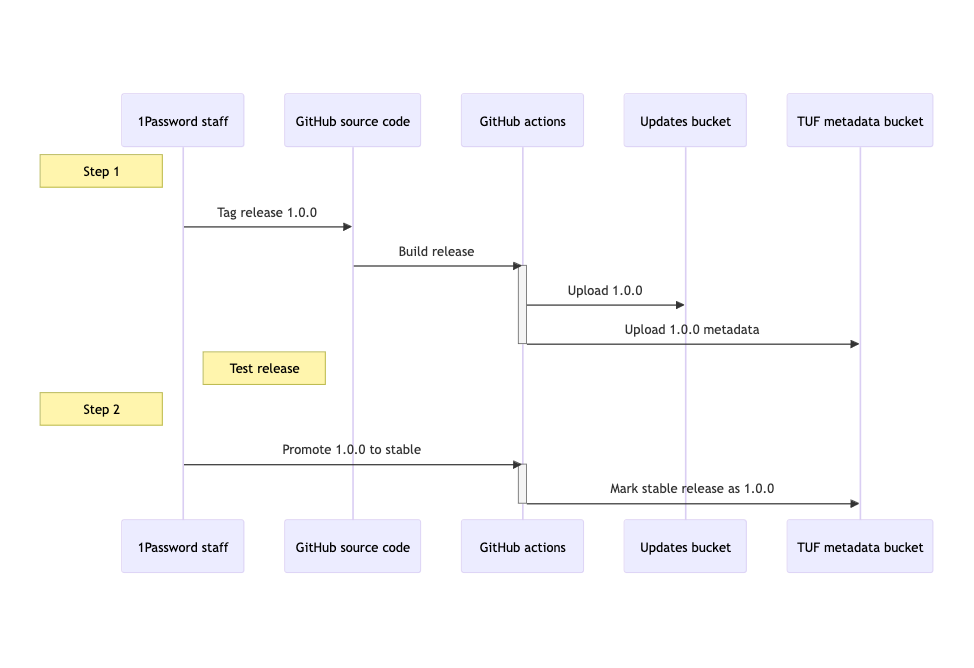
Making an update available is a two-step process. The first step is the upload of the tagged update itself. The second step is promoting that tag to the stable release channel, which will tell the 1Password Device Trust agent that there is a new update to download.
First, we tag a new release (for example, v1.0.0 in the diagram above), which then kicks off a series of GitHub actions to perform the upload. The update is built, signed, notarized (for macOS), validated, and uploaded to the download bucket. Then, we use the go-tuf package to compute the corresponding metadata for that update, and upload that metadata to the TUF metadata bucket.
Before proceeding, we test this update to ensure it is safe to release. At 1Password, we use our own software – so each employee on the device trust team runs this new update for at least a week and reports any issues they see. The engineering team runs automated tests against this update, and also performs manual release validation against this update on macOS, Windows, and Linux devices.
Finally, once we have determined the release is ready to be promoted to the stable release channel, we again use GitHub actions to update the TUF metadata for the stable release channel, indicating that the tagged update is our new stable version.
How does the 1Password Device Trust agent download and verify updates?
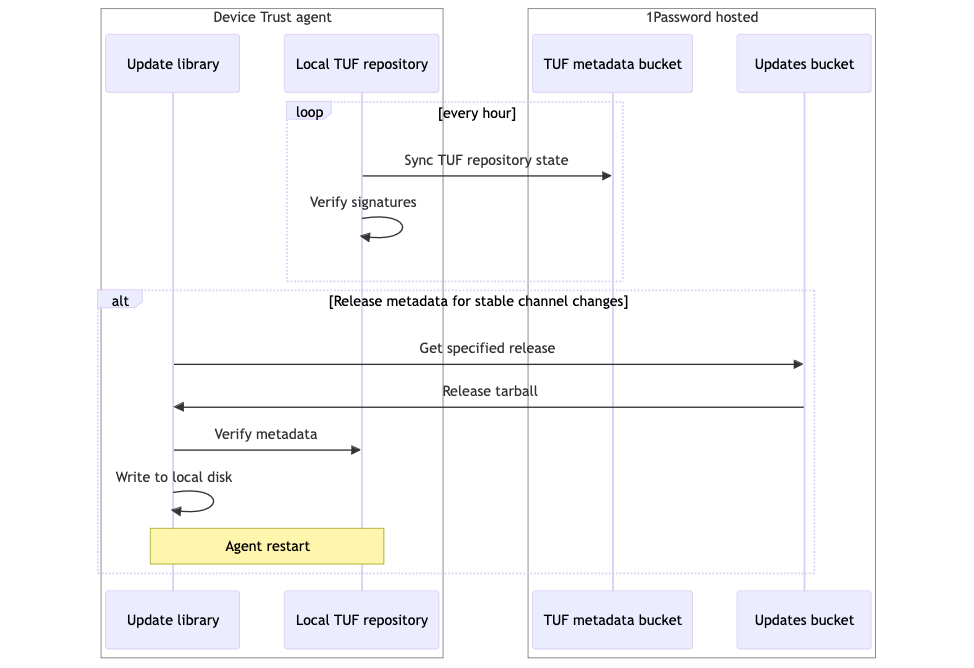
The 1Password Device Trust agent ships with a set of files representing a known, verified state of our TUF repository.
While the 1Password Device Trust agent runs, it periodically downloads and verifies incremental, sequential metadata updates to sync the state of its local TUF repository with the state of the metadata in the TUF metadata bucket.
The agent checks after each sync to see if the release metadata for the stable channel has been updated to point to a new version as the stable version. If it has, the agent will download the corresponding update from the download bucket. It then validates the downloaded update by comparing the update’s metadata against the known, authentic metadata for that update stored in its local TUF repository. If the update is valid, then the agent writes the update to disk and runs it.
Conclusion
1Password uses an audited update framework to record identifying metadata about each Device Trust agent update, and the agent itself uses the same framework to validate the updates that it downloads before storing or running them. The result is a secure autoupdate system that doesn’t require any effort from the user to ensure the 1Password Device Trust agent is running the latest stable update.
Want to learn more about how 1Password Extended Access Management works? Schedule a demo today!
 by Becca Mahany-Horton on
by Becca Mahany-Horton on