Just how strong should a 1Password account password be? We recommend that account passwords be generated using our wordlist generator using passwords that are four words long. This gets you something like “napery turnip speed adept”.
Among other things, this gives you the chance to learn new words. My dictionary has now informed me that “napery” means household linens such as table cloths and napkins. But let me move on from obscure vocabulary to asking about 1Password account password strength: What we know about account password strength, what we would like to know about it, and how can we get expert password crackers to help us learn?
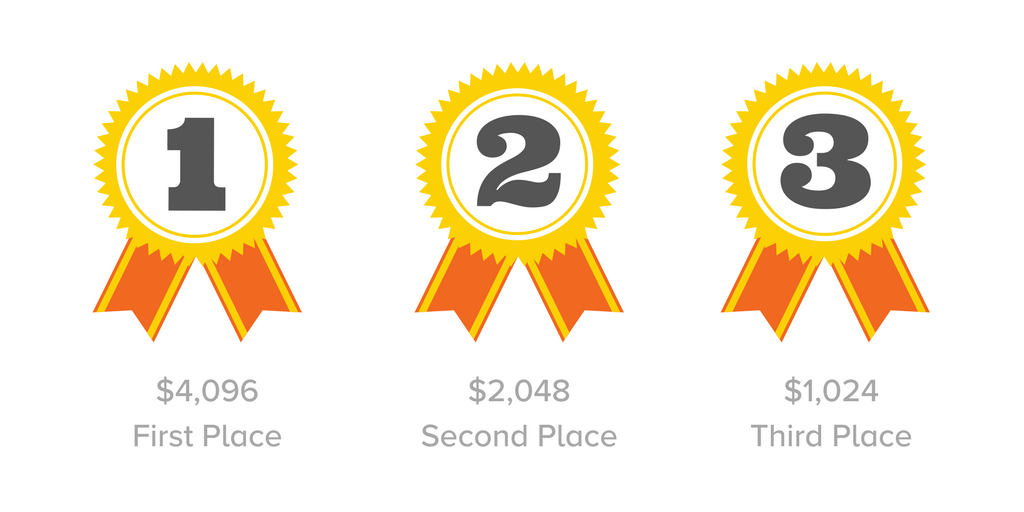
That’s why we are announcing a password cracking challenge to be managed by Bugcrowd with cash money rewards. First prize earns $8192, second prize is half of that, and third prize is half again. The race will begin has begun at noon Eastern Time on World Password Day, May 3, 2018. For those who want to jump right to the contest details, without reading the rest of this, you can head right over to our Bugcrowd brief or to our description. The challenge hashes/keys are now available.
What is your 1Password account password for?
Your 1Password account password is your defense against someone who manages to steal your encrypted 1Password data from your own machines. Your data on our machines is also protected by your Secret Key, making account password guessing futile. Unlike a human usable password, your Secret Key is completely unguessable, and that is what makes what is stored on 1Password.com uncrackable.

But your Secret Key does not protect you if data is stolen from your own devices because your Secret Key is stored on your own devices. Likewise, our Multi-Factor Authentication only defends against attempts to connect to our systems. MFA doesn’t protect you from data acquired from your own machines. So when it comes to keeping 1Password data stored on your own machine from prying eyes, your account password is your defense. It needs to be as strong as you can reasonably use and it must be unique.
Consider Molly (a not all that bright dog), who has a 1Password account password of “RabbitHunter#1”. She also has some very important Login items, such as her PawPal account within 1Password. Now suppose that Mr Talk (the neighbor’s cat) has contrived to steal data off of Molly’s laptop, including her encrypted 1Password data.
Mr Talk will set up automated password guessing software to make many thousands of guesses per second. We can slow that down with PBKDF2, but Mr Talk is doing everything on his own machines and is not connecting to any of our systems. That is why MFA doesn’t do Molly any good in these circumstances. Now if Mr Talk has some expertise in password cracking and is willing to dedicate some computer power to this, he might be able to crack that account password within a few hours or maybe it would take a week. However long that is is how much time Molly has to change her PawPal password and other passwords that she keeps in 1Password.
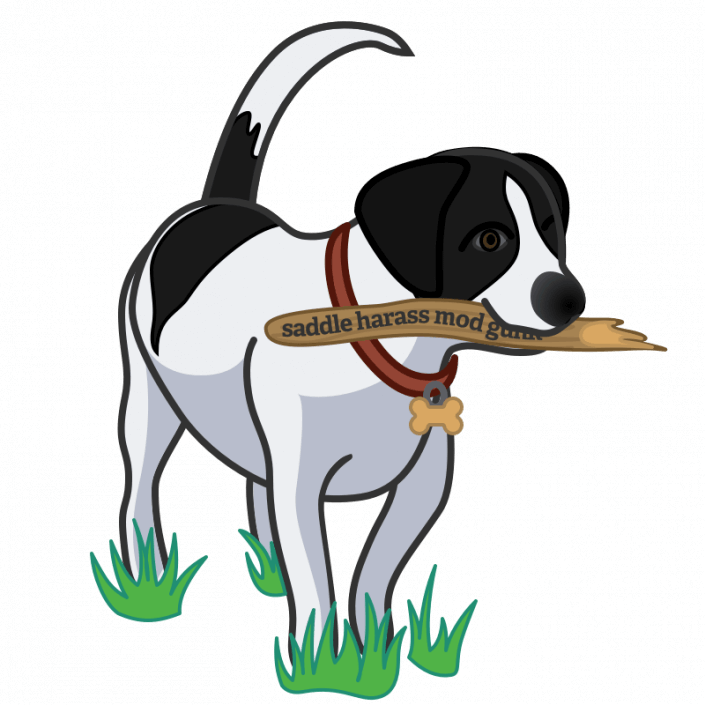
Let’s suppose that Mr Talk got Patty’s data as well. But Patty (a clever dog) used our Strong Password Generator and ended up with a 1Password account password of “saddle harass mod gunk”. Even if Mr Talk dedicated enormous amounts of computer resources to this, it would take decades or centuries to crack that. So Patty remains safe because she used a strong, randomly generated account password.
Again, for Mr Talk to have a whisker of a chance of cracking any of these passwords, he’d need to get data directly from Patty and Molly’s system, which will also provide Mr Talk with their Secret Keys. Mr Talk would not be able to launch such an attack from data acquired from our systems.
Reducing the guesswork by measuring the guessing work
How did I come up with saying “hours to a week” for Molly’s and “decades to centuries” for Patty’s? I did so with a lot of guesswork. But we’d like to improve on that guess work, and the way to do that is to invite (incentivize) expert crackers to try to crack passwords and find out just how much work they have to put into it.
Now if my guess about decades is anywhere on target for the four word password, that is simply too large of a challenge. So we are presenting a number of keys derived from three word passwords from our password generator. We are also posting all the details about how they were generated and the wordlist used.)
We are also simplifying some of the odd details of our key derivation function to focus solely on the 100,000 rounds of PBKDF2-HMAC-SHA256. This will make it easier for participants to get set up without really affecting the result of what we are trying to measure with this exercise.
We want winners
We want people to win the prizes, and we want people going into this to know that we want people to win. Otherwise we wouldn’t get participants to put in the effort that we are trying to measure.
So let me remind everyone again, the challenges that we have created here do not have the protection of the Secret Key and they are using 1Password account passwords that are at the weaker end of what we recommend. This contest simulates attacking only one single component of 1Password security.
Knowing your system is a good thing
It’s been nearly seven years since we helped revive the notion of wordlist-based passwords with this article. And one of the many virtues of generated passwords is that they remain strong even if the attacker knows how they were generated. So with that in mind, we are also publishing the source used to generate the challenges.
How long until we have answers?
If we knew how much effort it takes to crack a three word password, we wouldn’t be giving away money to find out, would we? We also don’t know what kinds of resources people will throw at the problem. If people or teams dedicate fleets of hashing rigs at the problem they will find things more quickly than someone who just uses a couple of more ordinary computers.
Money is time
It may be more useful to ask about the cost of cracking a password versus how much time it takes. In any particular cracking attempt there will be some combination of fixed costs and variable costs ranging from developing the expertise and equipment depreciation to the cost of the electricity used to run and cool the machines. We want to develop an estimate that considers the total cost. So we hope that the challenge takes long enough that the results will show a useful mixture of fixed and variable costs.
We’ve also structured the contest as a race. The first to find a password will earn $8192 $12288, while the second place prize is $2048 $8192. The third place prize is $1024 $6144, And the fourth place prize is $4096.
My own wild guess is that it could take anywhere between $250 and $2000 worth of effort to crack one of these three word passwords from our list, and so we’re offering a first prize that is double the higher end guess. This way it should be worth their time to switch some of their coin mining rigs over to password cracking.
Update: Nearly three months into the contest it is clear that I underestimated the cost. We have increased the prizes twice by now (July 26, 2018), and are still not certain that it is enough. Join us and participants in the forums for discussion of updates in cost estimates and how we may ensure that this challenge is worthwhile to participations.
What now?
If you would like to participate, head over to Bugcrowd for the official rules and to get set up with them if you are not already a Bugcrowd researcher, as all submissions will go through them. Details can also be found in our crackme challenge Github repository.
If you’d like to just follow along at home before and after the starting gun on World Password Day, keep following us on Twitter, Facebook, or your favorite place to do such things. And if you would like to discuss things further, just join us in our discussion forums. We’ve set up a specific discussion in our Lounge for this discussion.
 by Jeffrey Goldberg on
by Jeffrey Goldberg on