Security and IT professionals know that keeping a business secure is no easy task.
Finding and implementing the best solutions and keeping them up-to-date can feel like a never ending cat and mouse game with unseen adversaries. But it’s no secret that one of the biggest cybersecurity risks is the employees themselves. According to Verizon’s 2024 Data Breach Investigations Report, 68% of breaches involved a human element.
People are one of the main vulnerabilities that have proven challenging to secure. After all, no matter how many policies you put in place, if you can’t get your team to follow the rules, it all might all be for nought.
Unless noted otherwise, all the stats included in this blog post are from the 2024 1Password State of Enterprise Security Report.
The human challenge of cybersecurity
Visibility has proven to be one of the biggest challenges to IT professionals in recent years. Where once employees were tied to a physical office where devices and apps used were under the IT teams purview, now work happens from any device in any location. As hybrid work and bring your own device (BYOD) became the norm for many, so did employees bringing in SaaS apps that enhance collaboration and improve productivity. Suddenly, keeping track of and protecting against potential entry points can start to feel impossible.
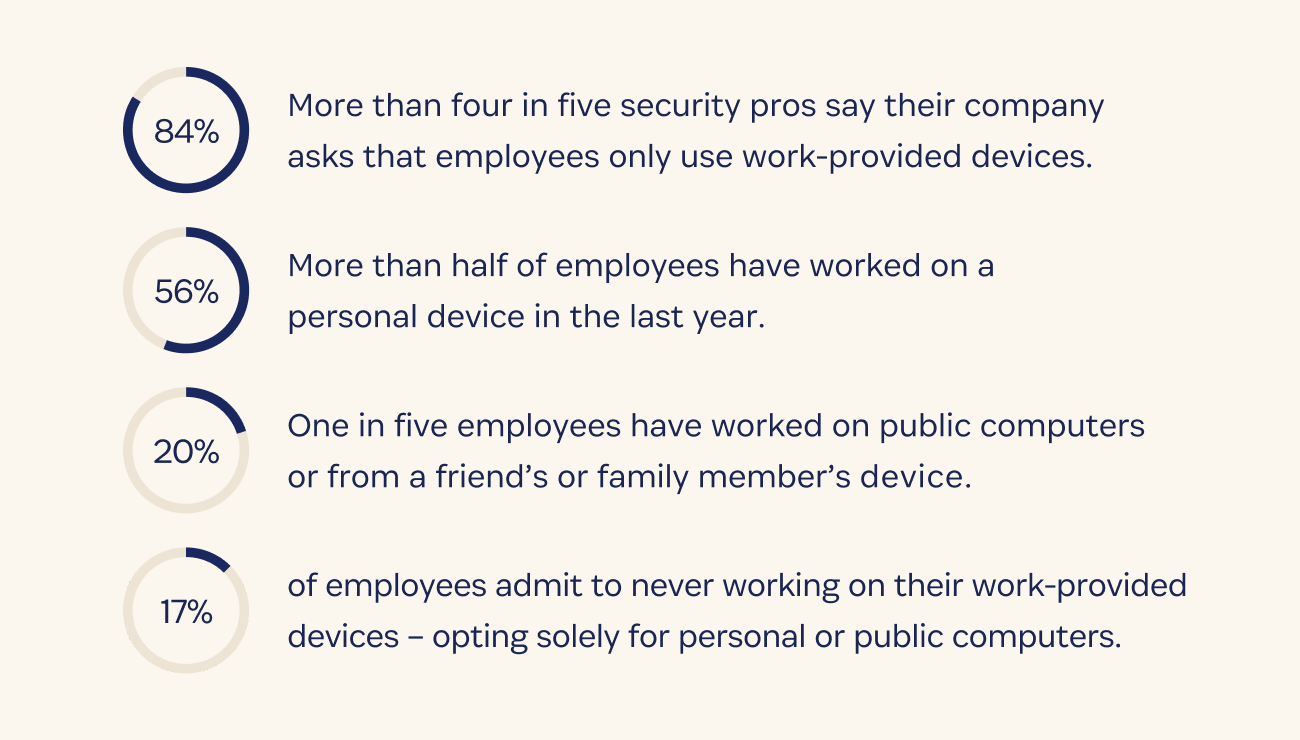
More than 90% of security pros say their company security policy requires IT approval to download and use software and apps for work. But, despite having rules in place, 34% of employees are still choosing to use shadow IT – unapproved SaaS apps.
There’s also the challenge of device management. Similar to IT security policies around app usage, organizations have also implemented security requirements asking employees to exclusively use work provided devices. But our research confirms that workers are still working from their own personal devices, or even more worrying, from friends, family, or public computers.
The risks
The risks of employees dodging these policies can’t be understated. Workers using apps outside of the IT team’s sight could be exposing sensitive data for both the company and customers. And, in the event of a data breach on those apps, all that information is not only exposed, but your business’ incident response plan won’t matter because you likely don’t even know the breach affects you.
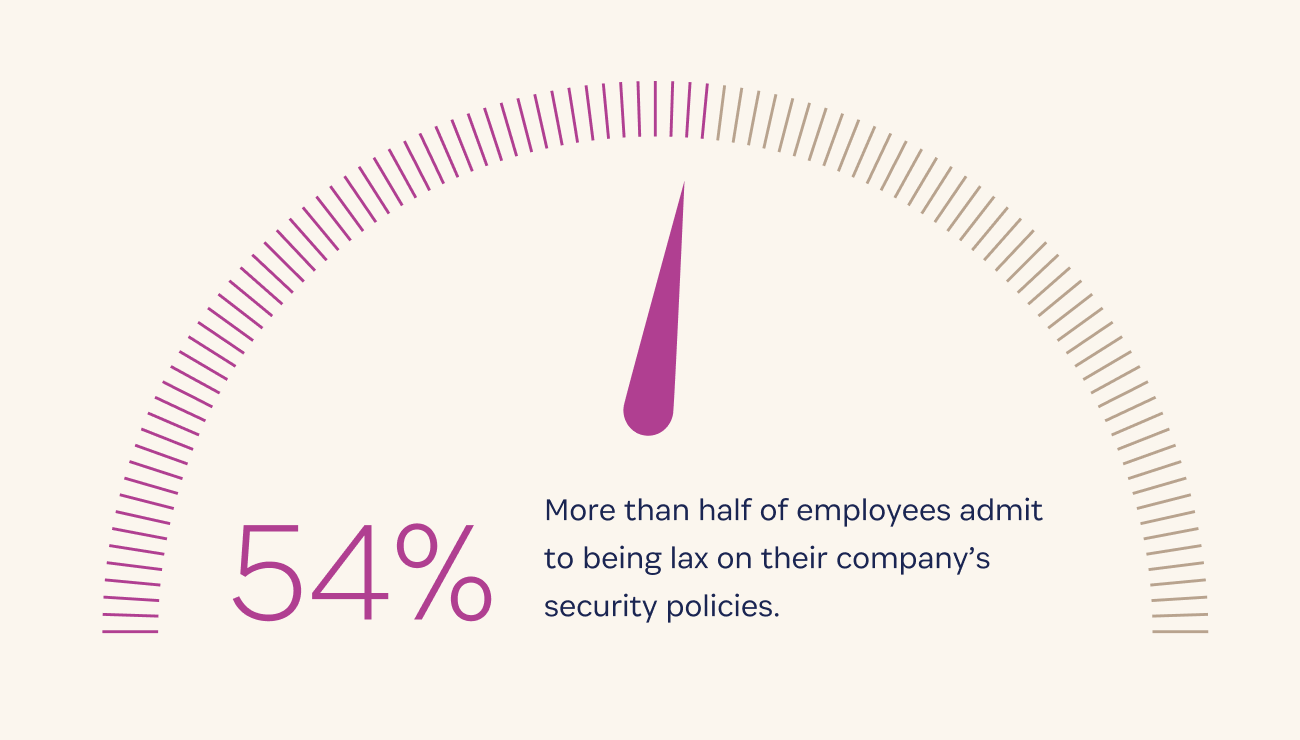
Many companies have worked hard to educate employees on why cybersecurity is important in an effort to encourage employees to make safer security choices. But with more than half of employees admitting to being lax on their company’s security policies, it might be falling on empty ears.
Why employees circumvent IT security policies
So if the risks are so high – and employees know the rules they’re meant to be following – why do they still choose to circumvent the IT security policy? If businesses want to improve compliance and reduce security incidents, they need to first understand why employees are finding workarounds.
According to the 2024 1Password State of Enterprise Security Report, 24% of employees say they’re just trying to get things done quickly and be productive. Other reasons workers are dodging security policies include those policies being inconvenient, too stringent, or unreasonable.
Employees clearly see information security regulations as barriers keeping them from getting their best work done. This lack of data security awareness isn’t deliberate on the employees' part – after all, they’re just trying to focus on the work they were hired for.
How to enforce an IT security policy
Now that we know what’s stopping employees from following security policies it’ll be easier to make sure your business is employing security controls that both improve visibility for IT teams, while also making it easier for employees to make smart security choices.
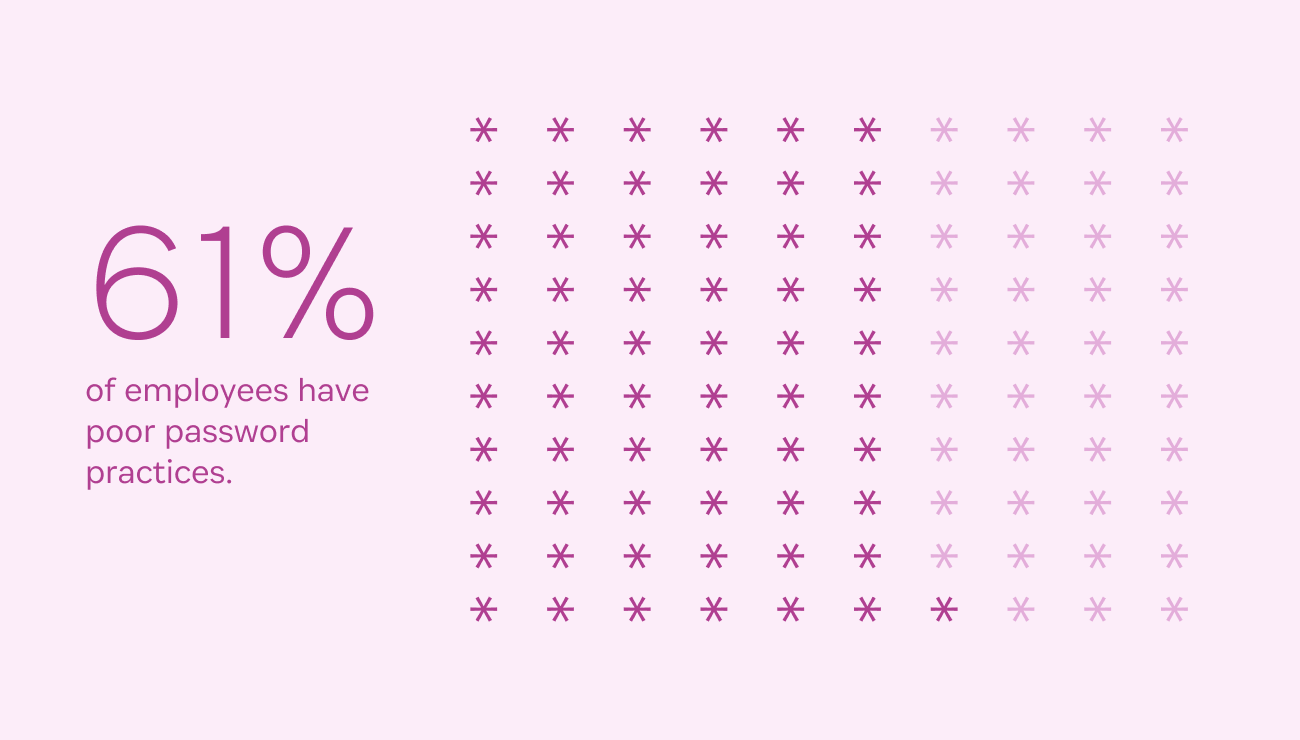
One of the best available security measures for protecting against shadow IT is a password manager. With 61% of employees exhibiting weak password practices it’s a tool that can have a large impact on the overall security of your business while also improving employee productivity.
For employees, a password manager makes signing in across apps and devices faster – letting them get to the task at hand sooner. It also makes sharing passwords and sensitive information with co-workers and contractors easier – helping improve collaboration across teams.
A password management tool also encourages strong security for all apps employees use – not just the ones approved by IT teams. And it keeps all employee logins in one place – so, if an employee needs to be deprovisioned, account ownership remains with the business.
Some password managers, like 1Password, also have reporting features that allow administrators to track actions performed by team members. For example, the Activity Log in 1Password Business allows administrators to see when team members view reports, set up new devices, invite guests to view items, and more.
1Password administrators are also able to enforce an information security policy, including requiring two-factor authentication (2FA) on accounts that have that option, and having rules around password strength and complexity on employee’s 1Password account. Employees get to work faster, and IT teams get to make sure work is being completed in a secure environment – it’s a win-win solution.
Enforcing an access management policy
But there’s more to identity and access management (IAM) than just protecting application sign-ins. Running a risk assessment will show that device trust and access control is becoming increasingly important as more employees choose to work from personal devices.

Extended access management moves beyond traditional IAM security tools and helps secure every sign in, on any device, from any location – all in one place.
Security teams looking for a solution that make it easier to secure unmanaged applications and devices need to look no further than extended access management. It’s a non-intrusive solution that empowers employees to work in whatever way is most convenient for them, without putting the business security at risk.
1Password Extended Access Management – the most complete solution available – allows administrator teams to manage access permissions for all types of identities, applications, devices, and users. With comprehensive visibility, administrators can protect against most threats, including data breaches – all from a single reporting center. With the ability to make sure only trusted users on secure devices have access with the ability to enforce policy and implement identity safeguards, the risk is significantly lowered.
We’re entering a new era of enforcing security policies – one where getting employees to say “yes” to good cybersecurity is no longer a question, but instead, it’s a given.

 by Stacey Harris on
by Stacey Harris on


