Password strength is a big deal. It is in fact one of the biggest deals. That’s why the Security Audit feature in 1Password pinpoints your weak passwords, so that you can go through and change them at your earliest convenience. But how does the strength meter actually calculate the strength of your password? What makes a password strong or weak? A recent conversation with a user inspired me to write down my thoughts on the subject. If you are going to trust 1Password to generate strong passwords for you, you should know how the strength meter works.
About Those Meters…
For a password strength meter to actually be accurate, it needs to know the system that was used to generate the password. When you generate a password using 1Password, we know that this newly generated password has been generated in a truly random fashion and can accurately calculate the password’s strength. However, when 1Password is evaluating the strength of a password that you have typed in manually, including a password which was generated in a truly random fashion on another device, the strength meter cannot know whether it is looking at a password that was created through a truly random process or created by a human.
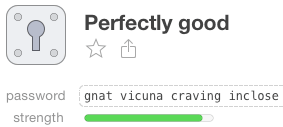
If our password strength meter sees something like “my dog has a bunch of fleas” or something like “gnat vicuna craving inclose”, it can’t tell that the first was probably made up by a human and that the second may have been generated by something smarter, like our password generator.
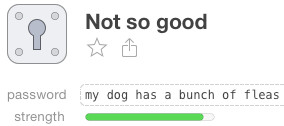
Because it doesn’t know how the password was generated, it errs on the side of caution. The strength meter will mark “gnat vicuna craving inclose” (a perfectly good password) the same as it will mark “my dog has a bunch of fleas” (not a good password at all). Both have the same number of letters (27) and both contain only lowercase letters. It’s up to you to know where the password originated. Did it come from our random password generator, or is it something a person made up?
Randomness and Selection Bias
When we speak of “randomness”, we are referring to mechanisms which have been tested and determined to be truly random and not dependent on events which may be repeatable or subject to outside observation. The toss of a fair coin or die is a source of “random input”. The radioactive decay of a substance can be used as “random input”. Our own limited vocabularies and choices of words are not “random input”.
When creating unique, strong, random passwords, what is required is a Cryptographically Secure Pseudorandom Number Generator (CSPRNG) to ensure that no one value or sequence of values will be preferred over all other values. The values from the CSPRNG may then be used to select from some alphabet or word list to create unique, strong, random passwords having the appropriate construction and length.
Selection Bias refers to preferences for specific values over others, whether by using an unfair coin, a loaded die, or a random number generator which does not produce a uniform and unbiased set of values. Inappropriate math performed on valid CSPRNG produced numbers may also lead to biases for certain values in favor of others. A common error is the use of modulo (remaindering) arithmetic which results in smaller values being used preferentially over larger values — there are more instances of values between 0 and 5535 (66 for each value) than between 5536 and 9999 (only 65 for each value) when using modulo-10000 on an unsigned 16-bit CSPRNG generated number.
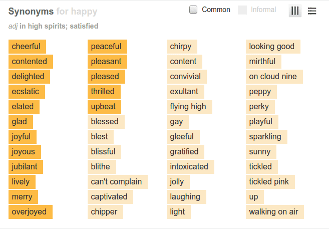
For human-generated passwords, common causes of selection bias include the use of a small and limited vocabulary (list all of the synonyms for “happy” you don’t use on a regular basis) and reuse of words (“cool”, “okay”) and avoidance of others (“groovy”, “hip”).
Pre-generated word lists avoid this type of selection bias by randomly selecting words which are common enough that the user should be able to spell the word from memory without being biased by personal preferences or regional differences in word choices.
Password Construction and Strength
The format of a password — the rules which are used to select characters or words — influences the strength of a password, but does not limit its possible strength, except to the extent that length limitations may be imposed on the result.
As an extreme example, consider a password that consists only of the letters “H” and “T”, and that you generate by repeatedly flipping a fair coin. If you make this password long enough it can have any strength desired — you only need to keep flipping a fair coin. But “long enough” in this case is actually unreasonably long. If you want a password that is as strong as a 10-character, mixed-case letter and digit password generated by our Strong Password Generator, your “H” and “T” password would have to be 60 characters long!
Memorizable Passwords
Shorter passwords from truly random sources can be stronger than longer passwords from biased sources even if they draw from the same character sets. For example, an 8-character, mixed-case letter and digit password produced by our generator is going to be a much better password than the longer (10-character) “Abcde12345” password that a human might come up with. There is reason to believe that the more “strength requirements” (use a digit, use mixed case, add a special character, etc.) we impose on people, the worse the passwords that they create may get. Part of this has to do with alphabet reduction: users may choose to limit mixed alphanumeric passwords to more alpha and less numeric, or more lowercase and less uppercase.
There is reason to believe that the more “strength requirements” we impose on people, the worse the passwords that they create may get.
For example, the rule “at least 8 characters, 1 uppercase letter and 1 digit” will produce approximately 80 billion (109) passwords (6 lowercase, 1 upper case, 1 digit: (26 * 26 * 26 * 26 * 26 * 26) * 26 * 10, or about 36 bits) if the uppercase letter appears first, followed immediately by a digit. But again, that assumes that the password was created by something that had a good random number generator and knew how to use it, and that the password isn’t simply a capitalized 8-character word with a single vowel replaced by a digit, such as “B3musing” (possibly as few as 14 bits). If the uppercase character and digit are allowed to be in any of the 8 possible positions, that increases the number to approximately 4,500 billion possible passwords (or about 42 bits).
This is a classic example of alphabet reduction where the complete rule should have been expressed as “at least 8 characters, 1 uppercase, 1 lowercase, 1 digit, and the remaining 5 chosen completely at random from the set of uppercase and lowercase letters, and digits”. When this revised rule is used, and a CSPRNG is used to select the characters, the number of possible passwords increases to ((62 * 62 * 62 * 62 * 62) * 26 * 26 * 10 * (8 * 7 * 6)), a total of about 2 million billion possible passwords (or about 50 bits). Each additional alphanumeric character, chosen completely at random by a CSPRNG, adds about 5.9 bits of additional strength.
Truly random length-limited passwords are hard for human beings to generate and memorize because people tend to choose less randomness in favor of greater memorizability. Using 1Password to generate and store passwords ensures that strong, unique, random passwords can be used without worrying about forgetting them.
Memorizable Passphrases
Choosing multiple words from a suitably large dictionary of words may result in stronger passwords even if all of the words appear in dictionaries, are spelled with lowercase letters, and no punctuation is used. Assuming a dictionary size of 20,000 common words (about 14.3 bits per word), chosen entirely at random, all of which are lowercase, the number of possible 4-word passwords increases to 160 million billion (about 57 bits.)
Studies of our ability to easily remember information have shown that we have limits to our ability to memorize seemingly random information, unless we have a useful mnemonic device or the information is grouped in a particular manner. This is why telephone numbers and postal codes tend to be grouped as they are, and why mnemonic devices are popular, such as “My Very Educated Mother Just Served Us Nine Pizzas”.
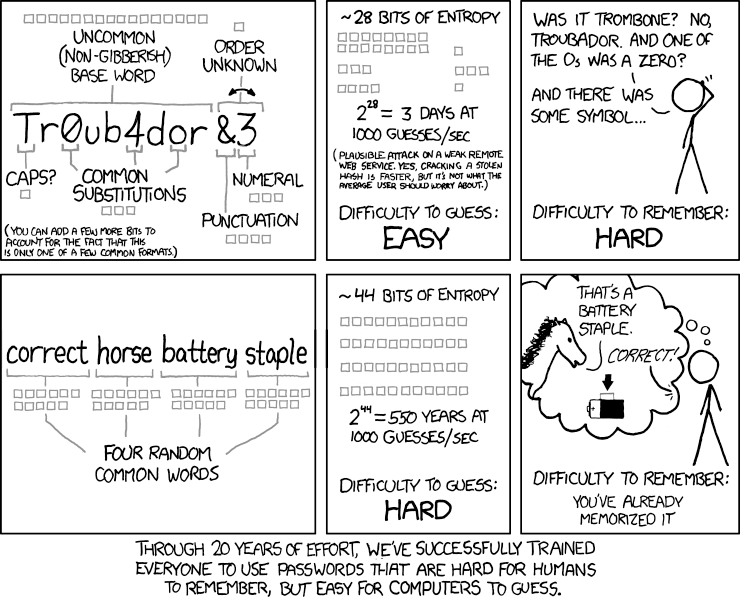
XKCD comic 936 is a perfect example of how easy it may be to memorize the random four-word password “correct horse battery staple”. As our Chief Defender Against the Dark Arts Jeffrey Goldberg will tell you, you may even add your own rules to that password to make it easier to memorize — “Correct! Horse: Battery staple.” Now you have a nice story to help you memorize a strong, random, unique password.
What It Means to You
Our strength meter (along with every other strength meter ever designed) has to guess how the password it is evaluating was created, unless you are actively generating the password in 1Password at that very moment. This means that you may see a big mismatch between “actual” and reported strength for our generated passwords.
The good news is that our password generator does a really good job of generating truly random passwords, so when you generate a secure, random, and unique password with 1Password, you know that it was generated just for you, right there on your device and it is as strong as can be for the length and rules you requested. So, let’s hear it for “paddle shrill sonorant palazzi ravioli” and “8dUaYolTJu82DDG9” — so happy to meet you, secure, random, and unique passwords that you are!
Additional Reading
For a more comprehensive discussion of generated password strength, please read the Geek Edition of our guide to creating better master passwords.

 by Julie on
by Julie on

