Corporate VPNs still provide value, but the rise of cloud-based SaaS apps have shifted the threat landscape since their heyday.
tl;dr: Many of the security concerns that made corporate VPNs a necessity in the 2000s are less important today. The rise of cloud-based SaaS apps have shifted the threat landscape, and security has broadly shifted to a Zero Trust model. Despite that, corporate VPNs still provide value and the companies that have them aren’t rushing to get rid of them any time soon.
Let me set the scene. As I write this blog post, I’m streaming music on Spotify and listening via Bluetooth headphones. This is a pretty big improvement from my youth, which was full of scratched CDs and tangled headphone wires. But I still haven’t gone totally digital; behind me sits an expensive record player and shelves full of vinyl. I love my record collection, and I’m not alone. The staggering numbers of LP sales show that vinyl has staying power, despite the availability of cloud-based alternatives.

Source: Rough Trade NYC’s line for Record Store Day 2023
This coexistence of the old guard and new is also taking place in the world of corporate data security. Think of records as corporate VPNs, and newer security models such as Zero Trust Network Access (ZTNA) as streaming apps. The older technology is still around, but the average user has shifted to remote connections that don’t require you to flip from side A to side B once the needle stops. (Okay, so it’s not a perfect 1:1 comparison.)
So what does that mean for the future of corporate VPNs? Where do they belong in today’s security stack?
The rise of VPNs
The advent of the corporate VPN can be traced back to 1996, when TechRadar writes that: “…a Microsoft engineer by the name of Gurdeep Singh-Pall developed the Peer-to-Peer Tunneling Protocol (PPTP). The goal was to use IP addresses to switch network packets and offer employees a secure and private means of connecting to their organization’s intranet.” This was before the widespread implementation of HTTPS, when unencrypted data intercepted via wifi was a huge security risk.
1Password VP of Product Jason Meller remembers that time.
“If you were on a public Wi-Fi or something like that, all of your traffic was just in the clear. Anybody who was on that same network could see exactly what you were doing and what pages you were looking at.”
“Companies were really scared about that. They were like, ‘Oh crap, people are going to be able to see the emails people are sending, or they’ll be able to figure out stuff if they’re listening to the network. We need to make sure all the traffic is encrypted.’ That’s what a VPN allowed for.”
VPNs allowed workers to break free from the physical office building while still maintaining a connection to its servers and the corporate network. In that landscape, it’s not hard to understand why, in the 2000s, VPNs were as ubiquitous as trucker hats and frosted tips. But innovation stands still for no one.
The VPN castle comes under siege
By the 2010s, the circumstances that created VPNs began to change. “The first thing that happened was mass proliferation of SaaS apps, and then the second thing was HTTPS got adopted everywhere,” says Meller.
Cloud-based SaaS apps were hosted outside the company’s network, and had their own logins and security protocols, instead of being routed through the VPN. And HTTPS ensured that all internet traffic was encrypted, which made it harder to justify paying for VPN as a secondary form of encryption, except in cases where employees accessed systems through vulnerable wi-fi.
VPNs were also incompatible with a new technology on the rise. “The executives all wanted iPhones,” explains Meller. “They wanted to get their email on their iPhones, and they weren’t willing to go do this whole VPN dance. Not only were they not willing, iPhones weren’t capable of even connecting to a VPN back then. So they started punching holes into them,” Meller recounts.
On top of that, VPNs had (and have) a fundamental security weakness: if one is compromised, the whole network is at risk. VPNs are part of a security paradigm commonly described as “castle-and-moat.” It’s a model built around the idea of a private company network, protected from the internet at large by firewalls, IDS tools, and VPNs.
Cloudflare describes the security model like this: “Imagine an organization’s network as a castle and the network perimeter as a moat. Once the drawbridge is lowered and someone crosses it, they have free rein inside the castle grounds.”
Now, to push the metaphor, imagine that drawbridge was highly flammable and prone to swinging open on windy days. As they’ve aged, corporate VPNs have become increasingly vulnerable; in fact, in 2016, 90% of SSL VPNs were found to be “hopelessly insecure,” according to researchers, with problems like obsolete protocols abounding. And of course, bad actors had never been shy about attacking VPNs, whether through ransomware or good old fashioned phishing.
Before we move on, let’s mention one final VPN flaw: they’re annoying. While they’re simple enough to roll out and implement at the admin level, VPNs are notorious for causing latency issues for end users.
For a long time now, forward-thinking security practitioners have wanted multiple choke points to stop threats, not a single entry/exit. And the explosion of cloud apps enabled just that – each had its own authentication process to control access, and even if one employee’s credentials were compromised on a single app, the others weren’t at risk. (That was the theory, anyway. In reality, poor password hygiene created its own security problems, and led to the rise of SSO, MFA, and passwordless authentication.)
Companies, specifically startups, faced a fork in the road, as an existing and tested security technology was beginning to compete against newer options.
Enter zero trust
In 2009, Forrester analyst John Kindervag coined the term “zero trust”.
Okta describes zero trust as: “…a security framework based on the belief that every user, device, and IP address accessing a resource is a threat until proven otherwise. Under the concept of ‘never trust, always verify,’ it requires that security teams implement strict access controls and verify anything that tries to connect to an enterprise’s network.”
Clearly, this approach to security is somewhat at odds with VPNs, where all users within a given network are treated as equally “trusted” as soon as they authenticate.
In 2014, Google unveiled its BeyondCorp initiative, and zero trust gained credibility as one of the biggest tech companies in the world decided it was good enough to protect them. And its popularity has only continued to mount in the decade since, culminating in a 2021 Executive Order rolling out ZTA at the federal government.
Increasingly, businesses started to circumvent VPNs altogether. The model shifted away from on-premises servers, closed networks, and office buildings, and toward SaaS applications, cloud hosted infrastructure, and remote work. “The reason we don’t use/have need for a VPN, is due to the fact we don’t have any self-hosted tools, software or servers and have a very IT literate team,” says Josh Barber, a Digital Specialist at 5874 Commerce.
The companies using VPNs today
But even as zero trust becomes the dominant model, the VPN has maintained a strong presence in enterprise security (even as infosec experts of all stripes have been predicting its “death” for over a decade now).
The COVID-19 pandemic was certainly the source of one recent bump in adoption. VPNs were a known quantity for companies scrambling to accommodate the sudden need for remote access. (It’s worth noting that the pandemic years also saw an increase of over 1,500% in the number of attacks against VPNs.)
And they’ve stayed the course since. In our own 2023 survey of knowledge workers, 79% reported that their company used a VPN for security; it was second only to MFA (80%) and well ahead of MDM (52%).
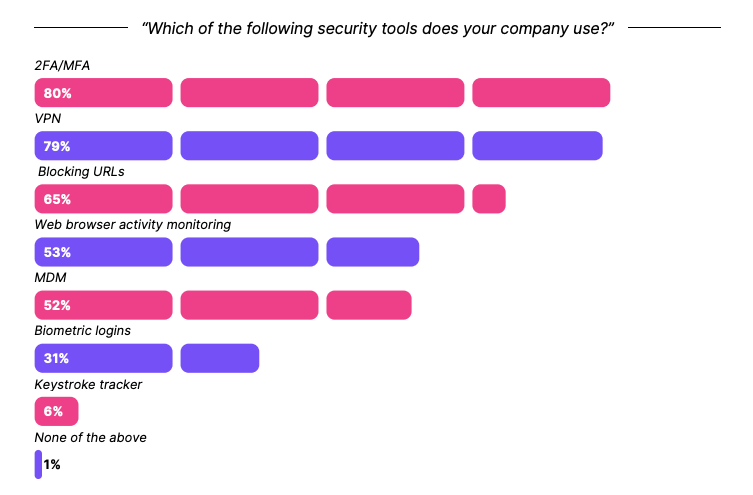
Source: The Shadow IT Report
As for why companies keep them, we went to the Mac Admins forum for insights.
A VP of Technology at a small analytics company still has a VPN in place, even though they use a majority of SaaS applications. They boil their VPN usage down to: why not? “[VPN] was easy to implement, and easy to maintain. And it provides an additional layer of protection when using untrusted WiFi [networks].”
The fact that VPNs are still the more familiar technology can also be useful for third-party compliance. As one IT manager said: “It’s easier to explain to auditors that your production environment is behind a VPN than it is to walk them through your zero trust platform.” (With the aforementioned executive order, growing familiarity with zero trust architecture, and growing anxieties around VPN vulnerabilities, their advantage in compliance may also see diminishing returns).
Some companies also keep VPN around simply because their customers demand it, as when a fixed IP is needed for a client’s server that has an IP whitelisted.
And of course, keeping on-prem servers – and VPNs to guard them – is still the most cost-effective option for some companies. That’s particularly true for legacy enterprises, although some younger and smaller companies also go that route. “We deal with large amounts of media that would be prohibitively expensive to have 100% cloud (print and digital publishing),” explains the IT Director of a medium-sized media company. “Hence the need for on premise storage and VPN to access that when not at one of our locations.”
But is the continued prevalence of enterprise VPNs a problem? The aforementioned survey from Cybersecurity Insiders also found that “62% of enterprises agree that VPNs are anti-zero trust.”
Are VPNs in conflict with zero trust?
If you’re a VPN fan, breathe a sigh of relief — if you’re still getting value out of it, you can keep it. Zero trust and VPN can coexist; they’re just designed to protect different things.
For instance, 1Password’s Device Trust solution falls within the zero trust ecosystem. In a nutshell, our product ensures that only trusted, healthy devices can access SSO-protected apps.
We don’t consider ourselves to be direct competitors with VPN, because even though some VPNs provide basic device telemetry, it’s not their primary function. We also don’t think that VPNs inherently conflict with our product, especially for legacy companies and industries using specialized or on-prem tools in addition to typical SaaS apps.
However, VPNs can let organizations get complacent about what kinds of devices access their resources. Most companies don’t want any ol' device logging into their resources, because it could be infected with malware or belong to a bad actor. But our research found that even though 79% of companies have VPN, 47% of them still let unmanaged devices access their resources.
Since corporate VPNs are typically only installed on company-owned devices, it’s easy to assume that any employee with VPN on their device is only working on that managed, approved device. But it’s just as likely that employees use their work laptops for the VPN and use their personal devices for all those SaaS apps outside the VPN.
The two can coexist, and even complement each other, but VPNs simply can’t provide the same guarantees that zero trust options can, like making sure that only trusted and secure devices access your sensitive resources.
Meanwhile, the security risks of VPNs are far from resolved, with reports showing the number of corporate VPN vulnerabilities (with consequences as severe as remote code execution) surging in 2023. Recent years have also seen a number of significant attacks on VPN, and the expectation is that they will only increase.
Overall, the choice to hold on or transition away from a VPN is mostly a matter of a company’s specific circumstances. But be sure you’re aware of your needs if you hold onto yours. A 2024 survey shows that 55% of companies surveyed have four or more remote access tools connecting their systems to the outside world. Some have as many as fifteen. And in many cases, that’s simply because they’ve held onto legacy systems that aren’t needed any more. Look closely at your VPN use, and be sure to make a conscious choice about whether to keep that drawbridge open.
Want to see how 1Password Extended Access Management manages access to cloud applications with or without VPNs? Reach out for a demo!
Disclaimer I: Quotes from participants have been modified for clarity and brevity with their permission and acknowledgement.
Disclaimer II: The author of this blog has frosted tips.
 by Kenny Najarro on
by Kenny Najarro on