What happens if someone gets hold of your encrypted 1Password data? What would it take to “crack” it? From the beginning, we’ve designed the 1Password data format with the knowledge that some people would have their computers stolen. I want to briefly talk about one of those design elements: PBKDF2.
The abbreviation PBKDF2 stands for “Password Based Key Derivation Function version 2” and does not stand for “Peanut Butter Keeps Dogs Friendly, Too”, but my dogs love peanut butter, and I do find the latter easier to remember. I need to remember “PBKDF2” because it is a very important, though behind the scenes, part of your security.
PBKDF2 deliberately slows down the process of getting from a password to an actual decryption key. The idea is to make using automated password guessing tools, such as John the Ripper, impractical. PBKDF2 strengthens what would otherwise the be weakest part of a system, your master password. PBKDF2 is called a “Key Strengthening Protocol” for this very reason.
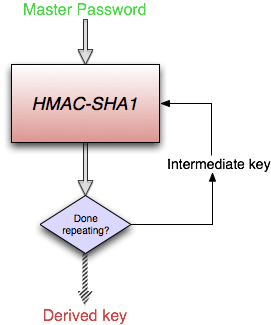
It works by forcing the process that goes from your master password to the derived key go through a large number of complicated iterations. Each time through the data is transformed using an encryption process called HMAC-SHA1, and the resulting intermediate key is fed back into the whole thing again.
For our current (1Password 3) Agile Keychain format, we’ve set things to use 1000 iterations. [Update: changed to 10000 in November 2012] Without PBKDF2, password guessing program could try hundreds of thousands of passwords per second, with PBKDF2 that number is dramatically reduced because there is no way to test a possible master password without having to perform all of those operations. PBKDF2 may cause a fraction of a second delay for you when you enter your master password, but that fraction of a second quickly adds up when a password cracker is trying millions of passwords.
As the environment changes, we are beefing our use of PBKDF2 even more in our next data format. Today, a good master password in combination with our use of PBKDF2 protects your 1Password data, even if it falls into the wrong hands. [Update: There have been several adjustments to PBKDF2 settings since this article was first published, as can be seen by various articles on this blog that discuss PBKDF2]
Coming soon will be a blog post about what makes for a good master password.

 by Jeffrey Goldberg on
by Jeffrey Goldberg on

