This is a story with many beginnings and many threads coming together. The very short read of it is that 1Password’s browser extension has always been designed from the outset to keep you safe from some recently discovered browser based attacks on some password managers.
Researchers at Princeton University’s Web Transparency and Accountability Project were investigating tracking scripts on web pages, and discovered that several of them attack browser-based password managers and extract the email addresses, usernames and sites stored in the browser’s password manager. As I said, 1Password is designed in such a way as to not be vulnerable to the kinds of attacks those scripts used. The scripts that attempt this are from Adthink (audience insights) and OnAudience (behavioralengine).
Whether or not they make malicious use of the passwords they extract, they are certainly learning which sites you have records for in those password managers. I would like to add that we’ve designed 1Password so that we cannot know which sites and services you have logins for.
There is a huge amount to say about the contemptible behavior of these trackers, and I’m hopeful that others will say so clearly. Here, I want to talk more about what all of this illustrates about 1Password’s design and our approach to security.
Saying “no” to automatic autofill
A commonly requested feature is an option that that would have 1Password automatically fill in web forms as soon as you navigate to those pages in your browser. 1Password, instead, always requires that you take some action. Perhaps it is just hitting ⌘-\ or Ctrl-\ or using our Go and Fill mechanism or even setting up a 1Click Bookmark. But whatever of several mechanisms 1Password makes available, you have to tell it that you want it to fill material on the page.
Plenty of you have written in over the years, saying that they would like 1Password to fill in web forms as soon as they get to a page, with no human intervention. We’ve even been told that it is a very popular feature of some other password managers.
It’s not a lot of fun saying “no” to feature requests. But that is what we have done for as long as I can remember. And for the rest of this article, I’m going to draw from something I wrote in our forums back in 2014.
Because of security concerns we are disinclined at this time to offer, even as an option, the feature you (and so many others) are asking for. […] but I do want to give you an overview of our reasoning for what might seem like an odd choice.
Automatically filling a web form with no user intervention other than visiting the page can, if combined with something that works around the anti-phishing mechanism [of 1Password], lead to an attack where lots your usernames and passwords are submitted to a malicious site in a way that is silent and invisible to you.
The longer answer
I will use the terminology adopted by David Silver and co-authors in Password Managers: Attacks and Defenses at the USENIX security conference (2014). In the terminology of that paper, this requested feature is “automatic auto-fill” instead of what 1Password does with “manual auto-fill”. That is, 1Password requires some user intervention before it will fill a form (such as you typing Ctrl-), instead of simply filling when you visit a page.
Although I am citing material from 2014, this kind of attack had been discussed since at least 2006, noting that
It’s really not phishing, as it doesn’t actually require the user to believe anything, as the social engineering portion of the attack is not there. As such you can steal user information through any page, as long as the automatic form submission requires no user input to fill the form.
This isn’t new.
Why am I now going to talk about phishing?
One of the great security benefits of 1Password is that it helps you avoid phishing attacks. When you ask 1Password to fill information into a page, it will not fill into pages that don’t match the URL of the item.
1Password has a number of mechanisms to prevent filling into the wrong page. That is, if you go to a form at paypal.evil.com 1Password will not fill in a password saved for paypal.com because the domains don’t match correctly. Tricking a person into filling out something like their PayPal password to something that only masquerades as PayPal is called “phishing”. The idea is that it should be harder to trick a password manager than a person. And it usually is. This is one of the many ways in which 1Password keeps you safe.
For the kinds of attacks we’ve been talking about, the malicious web page content needs to trick or by-pass the password manager’s anti-phishing mechanism. If a malicious script on MyKittyPictures.example.com is going to try to grab PayPal credentials, then it is going to have to fool the password manager into thinking that it is filling in a place that matches paypal.com.
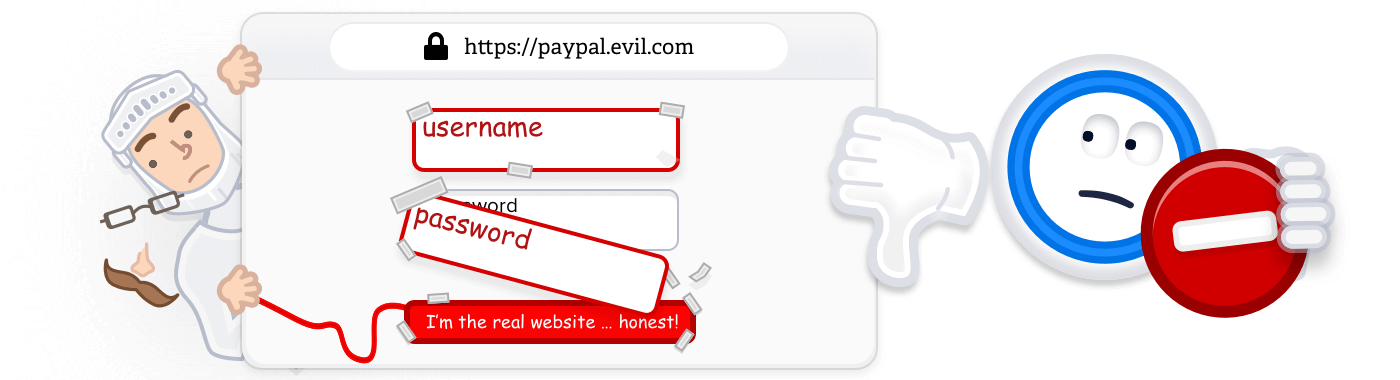
We work very hard to make 1Password do the right thing in such cases. 1Password’s anti-phishing mechanisms work very well at preventing it from filling into the “wrong” web forms. But because of the nature of the HTML, iFrames, protocols, javascript, iFrames, conventions, page designs, and iFrames, the defenses that we (and everyone) have to use are messy and involve a series of rules and exceptions and exceptions to those exceptions. (Did I mention that iFrames are a trouble spot?) It is exactly the kind of thing that we know can go wrong.
So the question we’ve had to ask ourselves is if the anti-phishing mechanisms are strong enough to mean that we never ever have to worry about 1Password in data to the wrong place. We needed to decide whether the tools available for that defense are strong enough to allow us to build a mechanism that meets our standards. Unfortunately they don’t, and so we insist on another line of defense.
Invisible forms
The fields in which usernames, passwords, credit card numbers, and so on get filled won’t always be visible to you. Any page could have a form on it that you don’t see. If the designer of the form is attempting to trick a form filling mechanism, there is no way that 1Password could actually check to see if the fields really are visible.
So if the anti-phishing mechanism can be tricked, then when you visit a malicious web page (including those that have malicious tracking scripts on them) you could have your private information silently and invisibly stolen if automatic auto-fill were in place.
Sweep attacks
The malicious form could be designed to reload itself spoofing a different password each time. So that is, a single malicious injection point could trick your automatically auto-filling password manager into giving up your passwords for many different sites. David Silver referred to these as “sweep attacks”, and that is what it appears that these advert trackers are doing.
At this point, I have not fully studied their scripts to know the precise mechanisms they used, but it certainly is some form of sweep attack.
Doing good and doing no harm
Here is where I go off on a bit of a philosophical abstraction. As I’ve said, I don’t believe that a password manager can offer 100% absolute protection against phishing. But suppose there is one attack out of a million in which it fails to protect against phishing. If you use 1Password, you are much safer against the other 999,999 attempts and you are no worse off than you would be without it. Even in that one in a million case, using 1Password doesn’t add to your risk.
But now contrast that with a situation with a password manager that does allow automatic autofill. A password manager that can be subject to a sweep attack enables a kind of attack that wouldn’t be possible without the use of a password manager.

If you are using a password manager that allows for automatic autofill, turn that feature off. If you are using a password manager that doesn’t allow you to turn that feature off, switch password managers. And when you consider making such a switch, please remember that we’ve never allowed automatic autofill at any time in our more than 10 year history. We believe that you have to be in the loop when it comes to giving your secrets to anyone else. That design philosophy helps keep you safe and in control.
It ain’t over till it’s over
I’m sure that there will be more news to come over the next few days or weeks about the extent of these malicious trackers and precisely which password managers were affected. So please follow in comments for more information.

 by Jeffrey Goldberg on
by Jeffrey Goldberg on