Our new command-line tool makes authorizing with services and securing your development toolchains easier than ever.
The magic of 1Password has always been making the secure thing to do the easy thing to do. Today I’m thrilled to announce that we’re bringing this magic to development teams everywhere with our new 1Password ssh agent and op command-line tool. 🦄
Use op to level up your shell by seamlessly providing secrets to all the services and accounts you use in your workflow.
Here we see op in action as we attempt to list our S3 buckets on AWS.
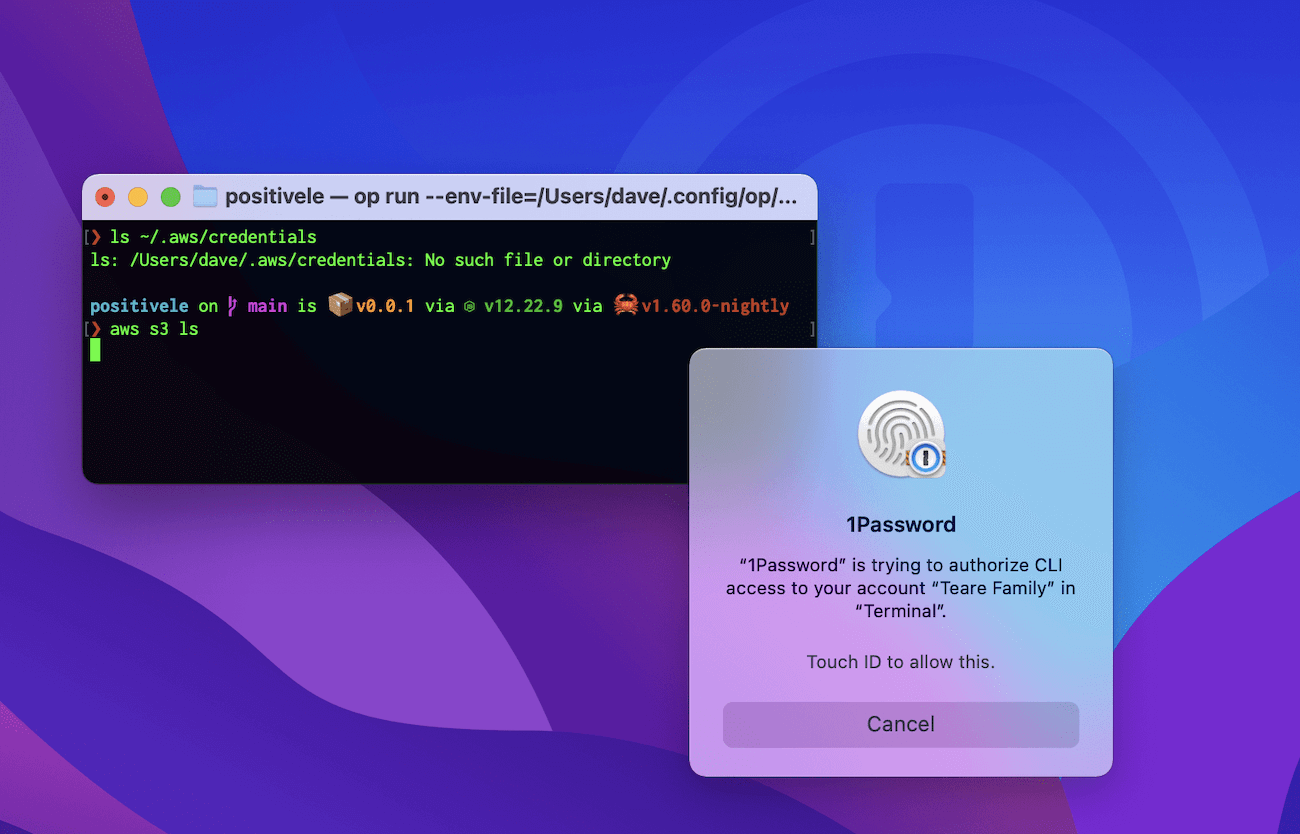
Did you see the magic? You need to look close as it’s easy to miss. 🕵🏻
You can catch a glimpse behind the curtain in the window title as aws is not being run directly. It has been aliased.
$ alias aws="op run --env-file=$HOME/.config/op/aws-env -- aws"
Now when aws executes it does so from within an op run context.
When it’s time to locate the access secrets aws does what it always does, but there is no (plain text) ~/.aws/credentials RC file for it to use. It does, however, find some magical $AWS_ACCESS_KEY_ID and $AWS_SECRET_ACCESS_KEY beans environment variables.
$ cat $HOME/.config/op/aws-env
AWS_ACCESS_KEY_ID=op://development/aws/access_key_id
AWS_SECRET_ACCESS_KEY=op://development/aws/secret_access_key
These variables use the secret reference syntax to specify that their values need to be loaded from 1Password. Inside the Development vault, within the AWS item, we see the fields access_key_id and secret_access_key have the secrets we’re looking for.

Behind the scenes 1Password finds this item and confirms that your shell program is authorized before giving the secrets to op, which in turn configures the ideal environment for aws to run within.
Even after knowing how the magic works my mind is still blown about how cool this is. 🤯
Let’s see what else we can do with this sorcery.
Automatic one-time passwords
Many systems tried to overcome the inherent insecurity of plain text RC files by requiring you to enter a one-time password. While this improved security, it hurt productivity.
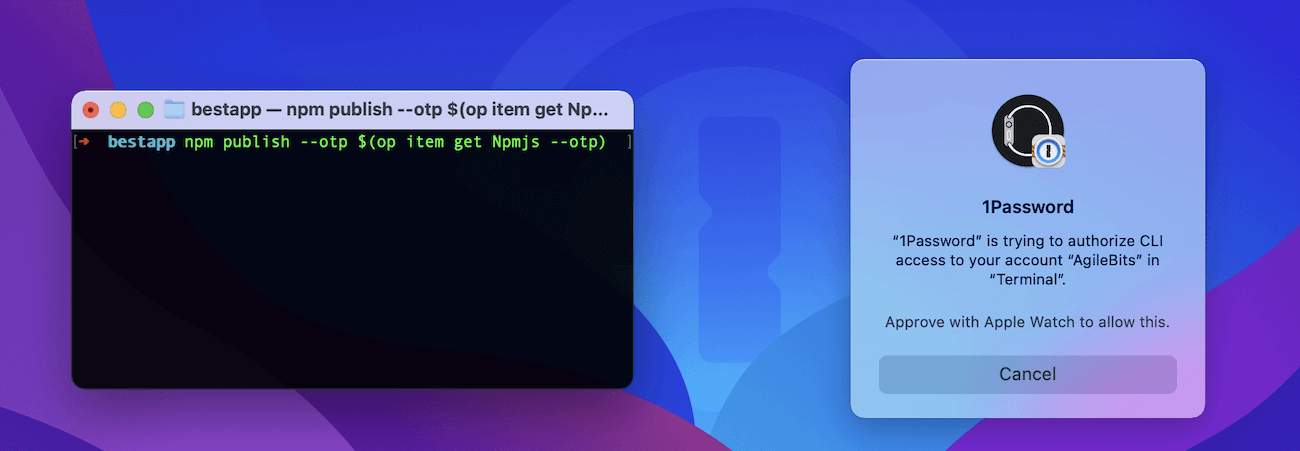
Thankfully op gives you access to everything you need during development or when publishing new releases, including TOTP codes. Let’s see how this looks for publishing an NPM package.
$ cat ~/.npmrc
//registry.npmjs.org/:_authToken=$NPM_AUTH_TOKEN
$ cat ~/.config/op/npm-env
NPM_AUTH_TOKEN=npm_FDQkqhf78jAcledwxxxxxxxxxxxxxx3vXdSH
$ alias npm="op run --env-file=$HOME/.config/op/npm-env -- npm"
$
$ npm publish --otp $(op item get npmjs --otp)
1Password will ask you to confirm access before proceeding. And if you have an Apple Watch you’re able to publish to NPM or anywhere else directly from your wrist! 😎
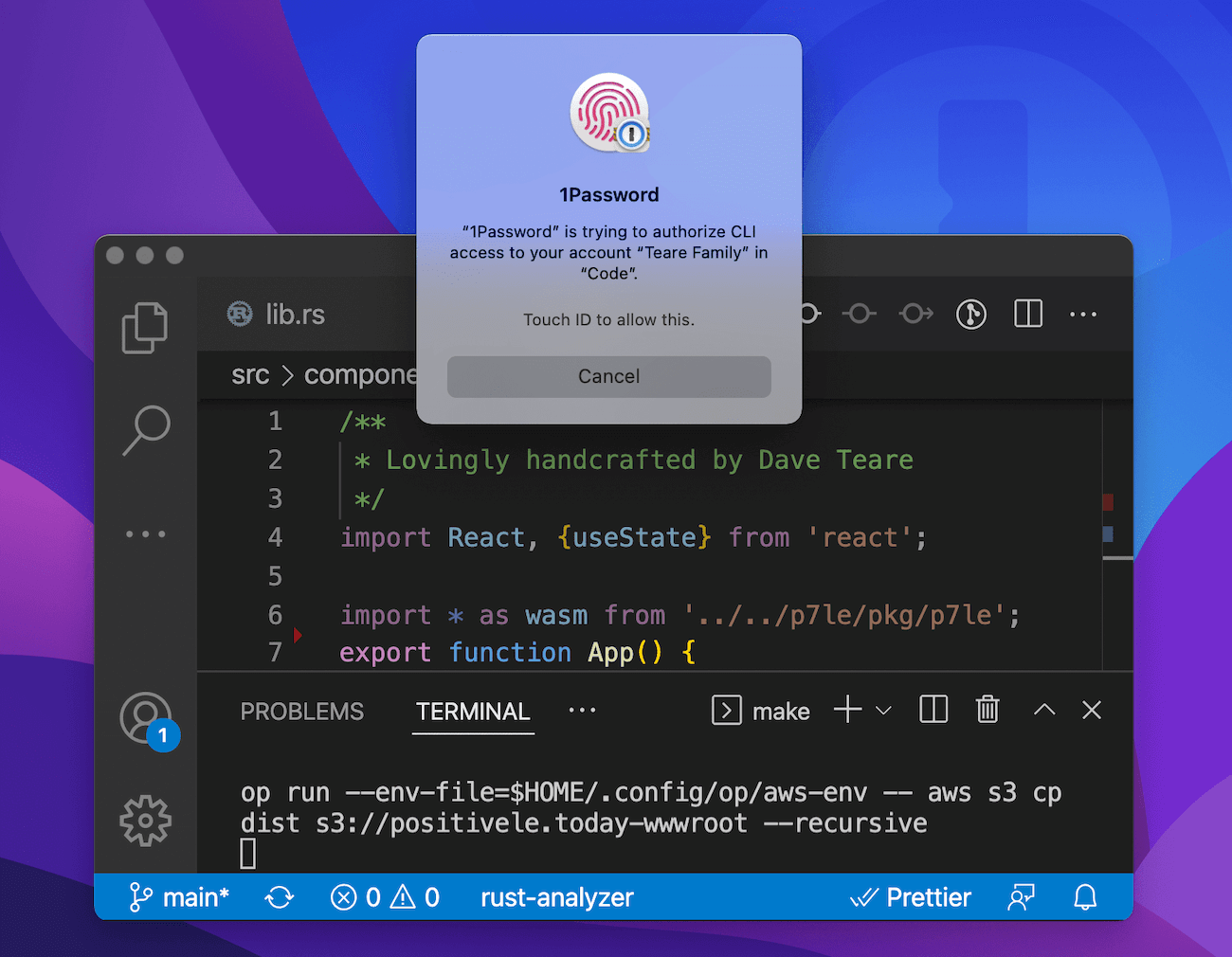
An OP IDE
IDEs are so powerful these days and with extensions you can do practically anything without switching apps. Manage your CI/CD pipelines and Docker containers, send Slack messages, browse Elasticsearch logs, or run deployment commands using the integrated Terminal.
All of these need secrets to connect you before you can get your job done. With op you can overpower your development environment and unlock an endless world of possibilities.
Here I am publishing my website, directly from within VSCode. 😍
And that’s just the tip of the iceberg. Check out Jody’s VSCode + 1Password extension demo for some truly exceptional wizardry. 🧙🏼
Co-op mode
With op you can grab credentials from any vault you have access to. This is magical for personal projects and becomes legendary in team environments.
Secret references can be committed to source control without worrying about leaking secret information, enabling everyone to share environment configuration files.
Go even further by creating a vault for shared secrets and granting access to your entire team. They’ll automatically receive this vault during onboarding and won’t need to worry about where to find secrets or how to store them securely. This greatly simplifies setup and ensures developers get up to speed quickly.
You can also easily revoke access when someone moves on to another project. Even better, everyone else will automatically get the new credentials after you rotate them, without any interruptions. 🥰
Unleashed in 1Password 8
All of this and more is available today in 1Password 8.
And be sure to check out our SSH & Git, meet 1Password 😎 companion post that brings the same simplicity to SSH keys and Git setup as op does to the command-line.
We hope you enjoy using these new tools as much as we enjoyed creating them for you. Please let us know in the CLI forum or reach out to me directly on Twitter.
Also be sure to stop by our AMA on Thursday to meet the team behind these features. Moreover you’re welcome to [join our devs for some command-line demos and 1Password ssh agent usage]https://1password.com/webinars) on March 30th.
Free for OSS teams
1Password would not be possible without the incredible work of the open source software community. From Rust and Golang to React and Neon – and many more – we’re thankful for these free software projects and are committed to giving back.
In that spirit and as our way of saying thanks, open source teams can get a free 1Password account simply by opening a pull request against our 1Password for Open Source Projects repo. These accounts also include unlimited use of Secrets Automation. To date, more than 360 open source projects are using 1Password.
Share your creations and win! 🙌
We can’t wait to see what you create with op. The integration possibilities are endless and since op is a full-powered CLI, you’re able to go well beyond secret retrieval:
- Invite and confirm new users 💌
- Integrate with your identity provider using SCIM Bridge 🌉
- Deploy secrets to production environments with Secrets Automation 🔐
- Share items with your team or externally with secure share links 🤗
- Create, read, update, and delete items, vaults, or documents 🌈
Imagining these features linked together alongside some 1Password ssh agent magic and other tools has me giddy with anticipation. It’s like Game of Thrones Season 4 all over again. 🙂
Please share your creations with us using #BuildWith1Password and win some great prizes! We have an upcoming post dedicated to the contest and anything you create and share now will qualify.
Oh, and if you have fun creating things and enjoy what we’re building here, be sure to say hi as we’re hiring. 👋
Take care and stay safe out there. ❤️

 by Dave Teare on
by Dave Teare on


Tweet about this post